19.07.2022 - Last week, the number of reports received by the NCSC remained low. Several reports on so-called CEO fraud cases stood out. The attackers have adapted their approach so that only a small number of fake email addresses are used in order to attract less attention. It is likely that the timing of the current wave was chosen because of the upcoming summer holidays. Many tasks are carried out by deputies due to holiday absences and attackers know how to exploit this.

Generally, cybercriminals reduce their activities during the holiday season, as their attack attempts are often met with holiday absence messages during this period and are disregarded. However, there are also other types of attacks that can be carried out with greater success during holiday periods. In the case of fraud attempts such as CEO fraud and BEC, it is possible that holiday deputies are more easily deceived and are therefore more vulnerable to such scams.
CEO fraud (invoicing the treasurer ostensibly in the name of the CEO or association's president) and BEC (business email compromise: attackers hack into an email inbox and change the payment data in existing emails) involve infiltrating (injecting) a fake invoice into a company's payment process.
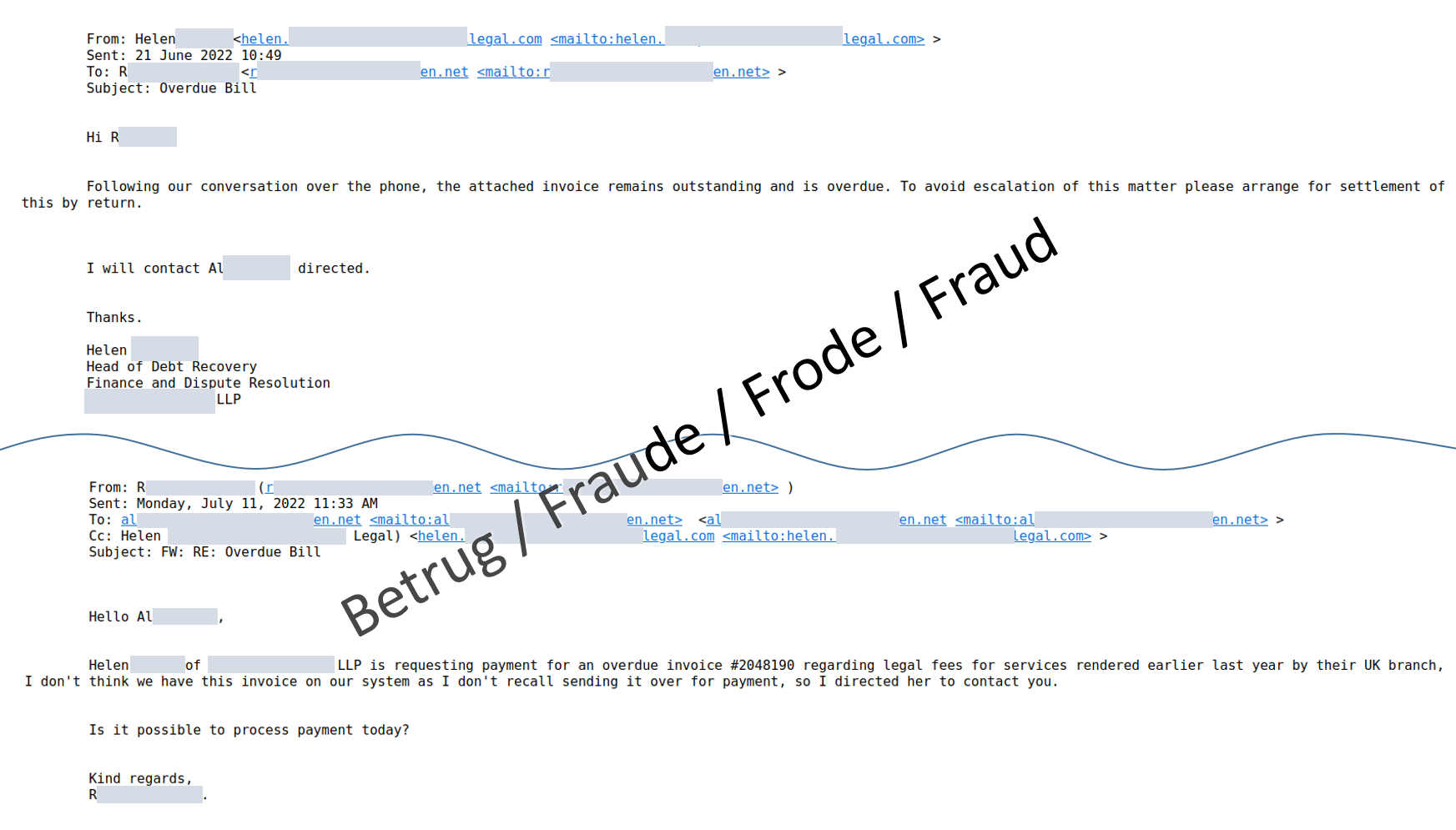
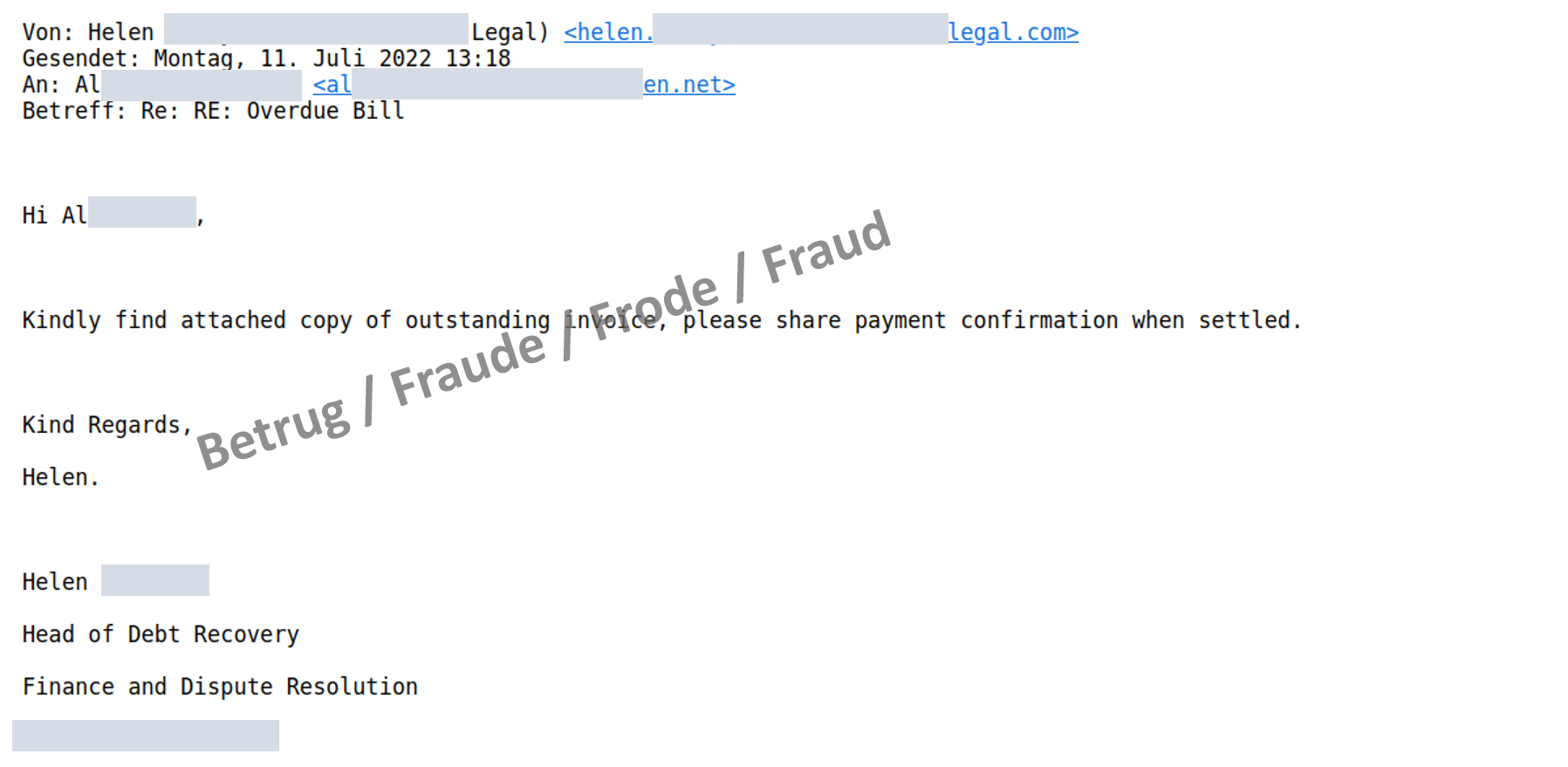
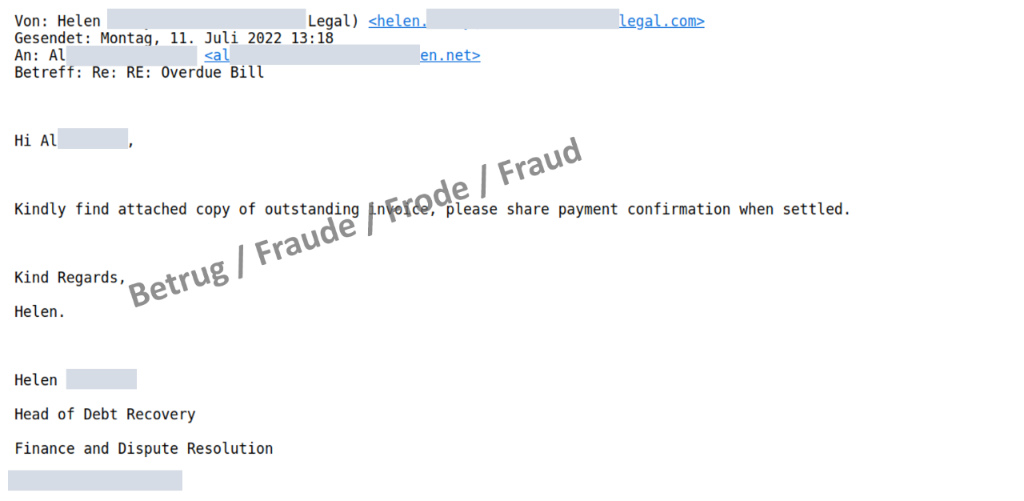
Last week, several such scams were reported to the NCSC. The fraudsters reserved a domain with a similar name, in our example the name of a law firm, which we will call "Legal", and created a corresponding email address (MX-record) for it, in our case name@legal.
In a second step, fictitious communication is created between an employee of the fake law firm (in most cases, the fraudsters use the name of a real person who works there – we call her "Helen" in this example) and the CEO of the company being attacked, in our case r*@*en.net.
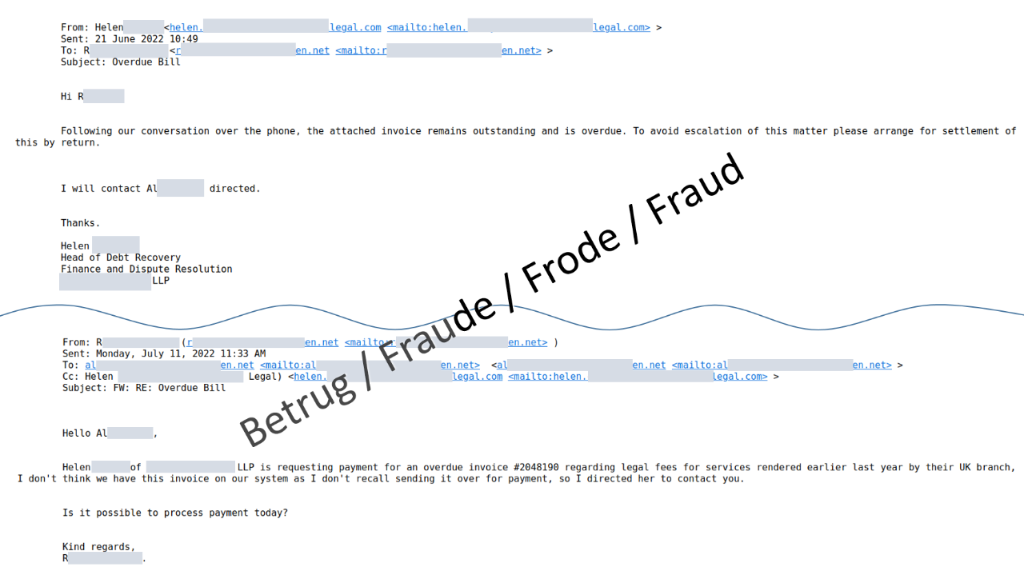
All email addresses used in this fake communication are correct – as it never happened in reality, but was fabricated extremely well. In the fake communication, "Helen" asked the CEO about an invoice that had allegedly not been paid yet. In the likewise fake reply from the CEO – which can now also go to the company's accounting department – the CEO seemingly acknowledged the invoice and instructed the accounting department to check the payment as quickly as possible and to make the payment if necessary.
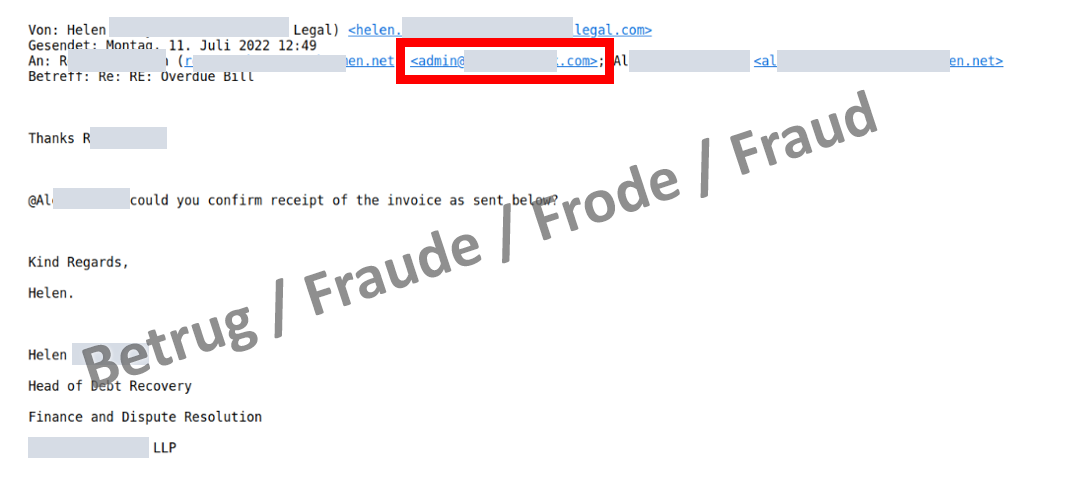
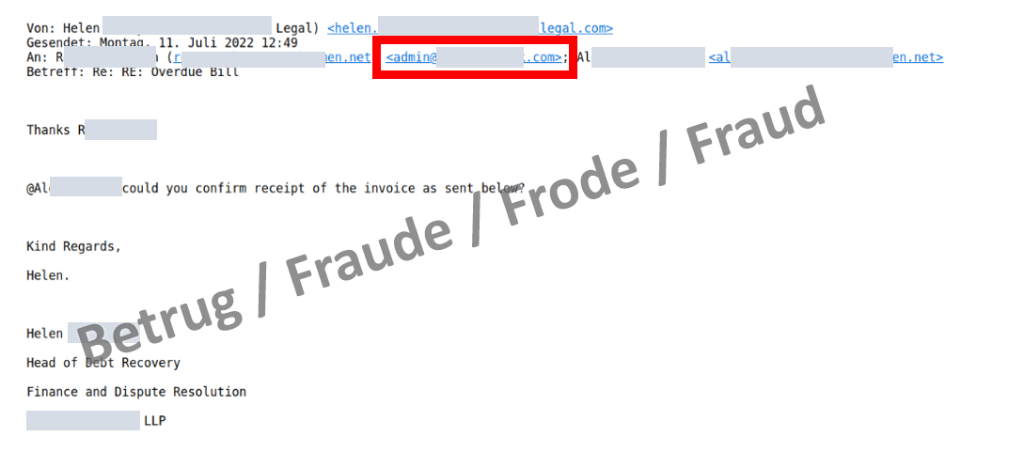
Shortly afterwards, "Helen" contacted the director again by email, thanked him for his support and asked the accounting department to process the transaction as soon as possible. However, in this email, the email address of the CEO had now been changed, so that a reply to all would not go to the CEO but rather to the scammers. This approach is new and makes the fake email addresses less noticeable.
From this point on, bogus "Helen" communicated directly with the accounting department, and the fraudsters had carte blanche.
The infiltration of a foreign invoice (injection) was successful, the accounting department processed the payment as usual.
In our case, the payment confirmation was then sent to the fraudsters and the CEO was CCed using his correct email address. This brought the fraud to light and the payment could fortunately still be stopped.
- Raise all employees' awareness of CEO fraud! Especially employees in finance divisions and in key positions must be informed about these possible methods of attack. In the case of associations, all presiding members and treasurers must receive training.
- Do not divulge any internal information and be careful with payment requests. Do not respond to unusual payment requests.
- All processes which concern payment transactions should be clearly defined internally and complied with by employees in all cases (e.g. dual control principle, joint signature by two people).
Current statistics
Last week's reports by category:
Last modification 19.07.2022