26.07.2022 - With the summer holidays in full swing, the number of reports received by the NCSC was again low last week. The NCSC received an increased number of reports of attempts to hack into systems using stolen login data; this form of attack is known as "credential stuffing". This can lead to interruptions because legitimate users are also locked out if too many attempts fail.

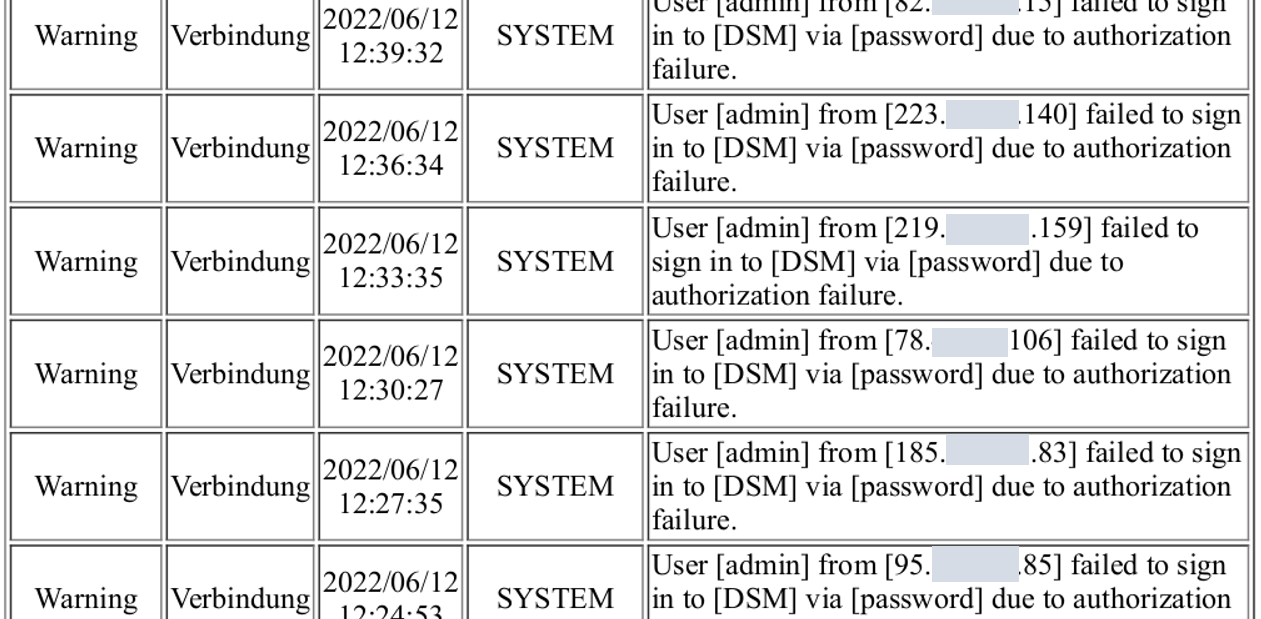
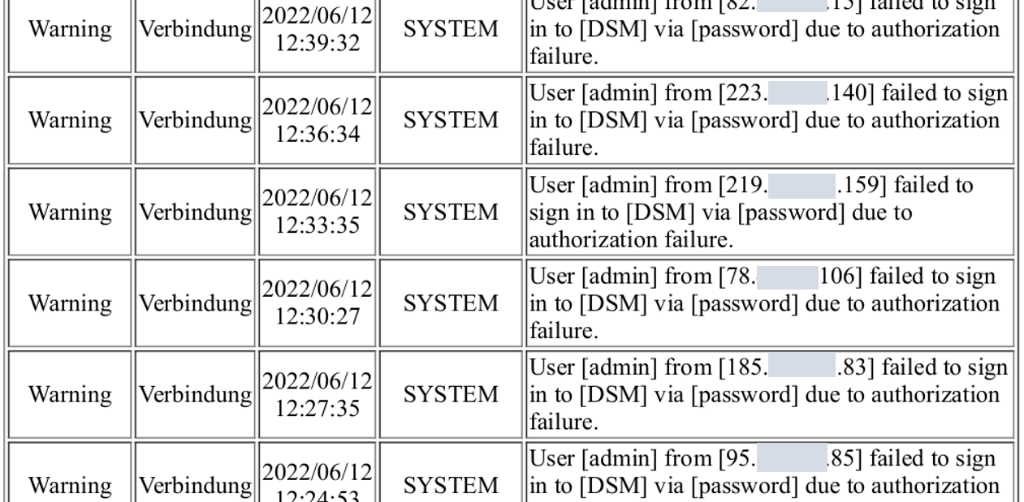
In recent weeks, the NCSC has received an increasing number of reports of suspicious entries in log data and service interruptions. It has been observed that different passwords are being tried out for different user names. This type of attack, in which stolen login credentials are used, is known as "credential stuffing". Repeatedly entering different passwords (stuffing) results in failed attempts, which means that users are ultimately locked out. This in turn can lead to service interruptions.
The attackers obtain previously leaked user names and passwords; such data can be accessed for a fee on the darknet, as well as publicly. Internet users can enter their email address on the website "haveibeenpwned.com" and check whether their data has already been leaked somewhere. This helpful service currently stores 11.8 billion records of leaked data of this kind. However, more recent data leaks are not yet available on the site; these are mostly offered directly for sale on the darknet.
Attackers can then use the stolen data sets to try to log in to various applications on the internet. This can be likened to the hackers having a huge bunch of keys in their hands and not knowing which key belongs to which door: they have to try every key in every door – or, for the internet, on every login page. Login pages are found everywhere where content needs to be protected, for example for accounts in online shops, for classified ad platforms, for payment services and many more. Login credentials are also used for industrial control devices that can be operated remotely via the internet, as well as for administrative access to routers, firewalls and other devices.
Hackers use all available sources to determine where the acquired access data might work. In doing so, they hope that users use the same login credentials for different applications. If, for example, the same email addresses turn up in social media channels, are used for product reviews in online shops or even belong to a company, these are indicators that the login credentials could be the same for all these applications and might also work.
Depending on the hackers' intentions, they then attack different targets. Some try to log into online marketplaces to commit small ad fraud and others try to use the login credentials to order goods from Amazon, Zalando and other online shops.
Hackers also like to select devices connected to the internet that secure company networks. For example, 1.3 million web consoles from the router manufacturer Netgear, which are used to administer devices via the internet, are indexed on the search engine "shodan.io" and can be accessed for such attacks.
Brute force attacks are somewhat different but have the same goal: the hackers select a specific account, e.g. "admin", and try all the passwords they can find or that may potentially work.
In order to protect yourself from such attacks, there are various things to bear in mind, both with regard to infrastructure and as a user of login credentials.
Protect infrastructure:
- Block login pages so that they cannot be accessed from the internet.
- Login pages for firewalls and network devices should only be accessible internally or via known IP addresses (e.g. your own VPN network).
- GeoIP fencing can be used to exclude undesired IP ranges (e.g. individual countries).
- After a failed login, the attacker's IP should be blocked for some time or the login attempt slowed down.
- Publicly accessible websites that require users to log in should be protected with so-called "captcha" technology. A captcha involves solving a small task so that humans can be distinguished from robots/bots.
The following always applies for your own login credentials:
- Always use a separate password for each online service.
- Use multi-factor authentication whenever possible.
Current statistics
Last week's reports by category:
Last modification 26.07.2022