16.05.2023 - Access to many applications and digital services is now protected with two-factor authentication. Smartphones are playing an increasingly important role in this. They are not only used to run applications and services, they are also often used to generate the second factor, be it through a one-time password generator or by receiving a text message. Therefore, cybercriminals are also increasingly trying to gain access to these devices in order to obtain all the required factors. In a recent report to the NCSC, the attackers used a technique called SIM swapping to do this.

Smartphones are becoming increasingly important in almost all areas of life. Their use is already central in terms of security, for example, to receive or generate a second factor when logging in. Therefore, attackers are keen on gaining access to a victim's phone in order to obtain all factors. The NCSC already reported in week 5 on how attackers are phishing for phone provider login data. With these credentials, the attackers can – in addition to using payment services – also carry out an attack called SIM swapping or SIM swap attack. One such case was recently reported to the NCSC.
What is SIM swapping?
The first thing the victim noticed was that it was no longer possible to access their email accounts. They therefore tried to log in directly to their webmail. This attempt failed because the second factor was sent but not they did not receive it on their smartphone. The victim then noticed that their phone number was blocked and that they could neither make phone calls nor send or receive text messages.
The victim subsequently realised that they had probably clicked on a phone provider phishing link and entered the login credentials without realising it was a phishing scam.
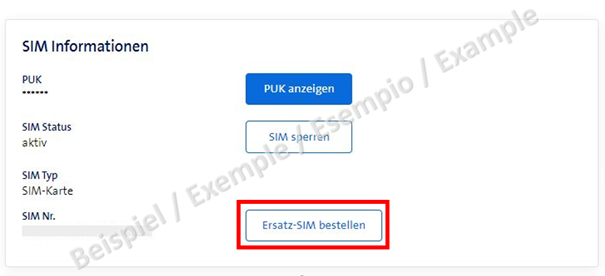
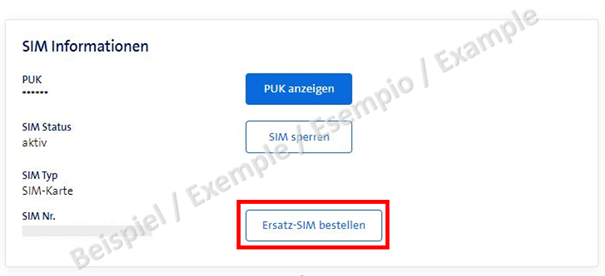
The attackers were able to log into the phone provider's portal using these intercepted credentials and order a new SIM card.
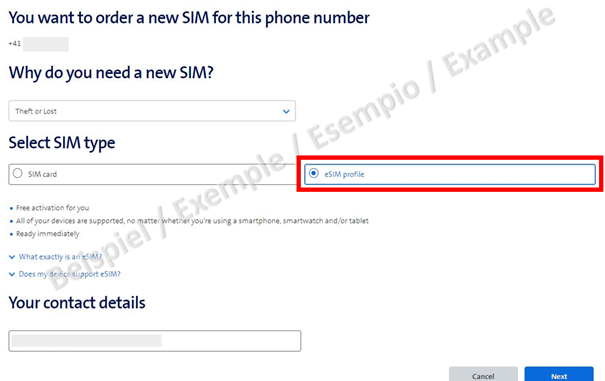
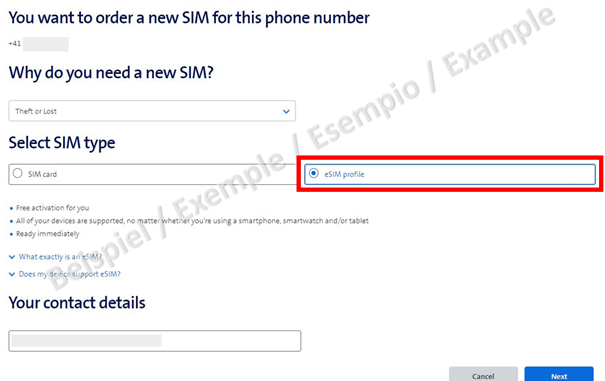
A physical SIM card or a new electronic eSIM can be ordered via the portal's order form. Since eSIMs with no physical support are only transmitted as a QR code, they can also be activated immediately on a new phone.
From then on, the attackers have access to all accounts that use this phone number. Second factors which are sent by text message can also be intercepted in this way.
The victim recognised the attack at an early stage as they had stopped receiving emails, and they were able to have the attackers' eSIM deactivated.
React quickly
You should react as soon as your login credentials for apps no longer work or you are logged out from active apps, you no longer receive social media messages or emails and you can longer send or receive phone calls or text messages, even though your phone indicates network reception.
- Beware of phishing messages in the name of the phone provider.
- Contact your phone provider immediately if you notice the symptoms mentioned in the last section.
- Enable multi-factor authentication whenever possible to add an extra layer of security.
- Never share your passwords and access code with third parties.
Current statistics
Last week's reports by category:
Last modification 16.05.2023