14.02.2023 - The number of reports received by the NCSC remained at the same high level last week. Attacks on Microsoft Office365 accounts stand out. These accounts are often secured with a second factor and are therefore harder to hack. So attackers are going to considerable lengths, using real-time phishing to obtain login credentials nonetheless. They use the stolen credentials to send phishing emails or for business email compromise attacks.

Real-time phishing of Microsoft Office365 accounts
Virtually all Microsoft Office365 access is now secured with a second factor. In addition to the email address and a password, a second factor – a code sent by text message or a token generated by an app – is required. However, the second factor is only valid for a limited period. So in order to steal the login credentials, the attackers have to act within a certain time.
A current example, which was reported to the NCSC last week by a communal authority, is described in more detail below.
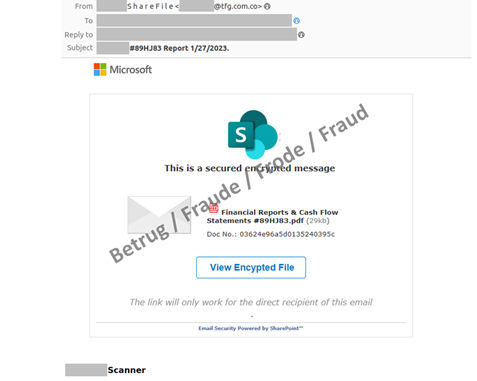
The attack began with an email which was disguised as a scanned document from a photocopier and claimed to contain a financial report in the form of an encrypted file.
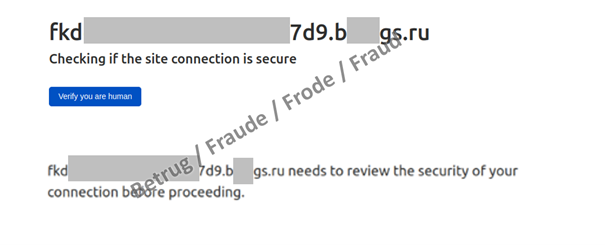
The attackers cannot be certain when the email was opened, or the phishing link clicked on. So in order to gain time and avoid having to react immediately when the victim clicks on the phishing link, the phishers first demand proof that there is a human behind the request. This enables them to prolong the login procedure slightly.
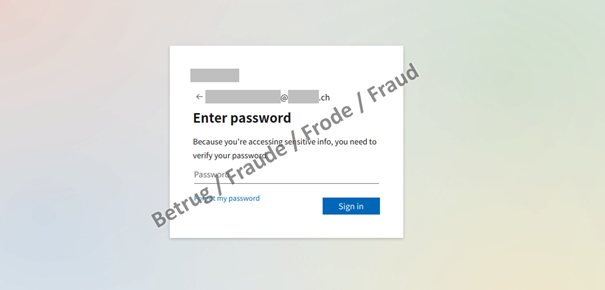
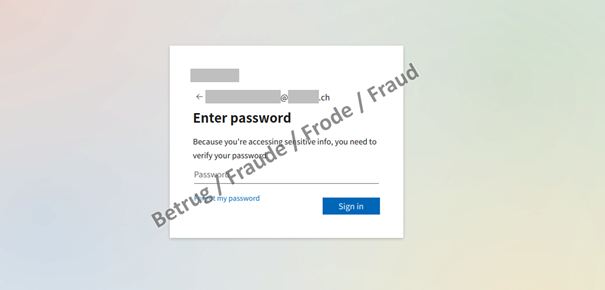
As soon as the victim clicks on the link, a phishing page bearing the logo of the company – or this case the commune – is generated dynamically and the victim's email address is displayed. After a correct user name and password are entered, the second factor is requested. For this purpose, the attackers log on in the background and trigger the text message or authentication token. They then load another page where this second factor can be entered.
If someone enters their login credentials on the phishing site, the second factor needs to be processed as soon as possible and automatically, so that the Office365 access thus obtained can be used.
Because of the second factor, this attack method is known as real-time phishing. The attackers cannot collect details for later use. They have to act immediately – i.e. in real time.
Having intercepted the second factor, the attackers can now log into the hacked account themselves and use it either in an automated process or "by hand". In this case, automation helps the attackers. For example, when automatic email forwarding is set up, emails are often sent to all contacts in the phone book. This increases the likelihood that other people will take the bait.
Things get really interesting when the hacked Office365 account contains emails with payment information or invoices. The attackers can use them to perform a so-called business email compromise (BEC) and change the account information in the invoices. So rather than the victim paying the invoice amount to the legitimate recipient, the money goes to a fraudulent account.
It is also easier to send software, since the recipients know and trust the hacked sender.
Luckily, the phishing attempt reported to the NCSC was not successful, owing to the perspicacity of the recipient.
Recommendations:
- Never enter a password or credit card number on a page you reached via a link in a message. It is most likely a phishing attempt;
- Check any website requesting your login credentials very carefully. Two-factor authentication does not protect you from real-time phishing.
Current statistics
Last week's reports by category:
Last modification 14.02.2023