30.01.2024 - Many internet users will now recognise phishing attempts when they see them. The main thing is not to click on the link: just ignore or delete the email or text message. Still, a lot of people are tempted to click on the link anyway and enter a made-up name or a password comprising a random combination of letters, just to give the scammers a hard time. This sort of data, which is totally worthless to scammers, then gets mixed up with real credentials stolen from unsuspecting victims. Before they can use or sell lists of stolen passwords, the scammers have to screen out all the junk data – and that takes a lot of time. So they are always looking for new tricks to keep their password lists as clean as possible.

Making you enter your data twice
After someone enters their username and password on a phishing site, they are then usually redirected to the real website. They probably just think that something went wrong and they log in again, this time on the real website. They may not see any reason to be suspicious and don't even think of changing their password. Increasingly, however, victims are now being asked to enter their password a second time on the fake page itself. They are then only redirected to the real website after the second or third attempt. What's behind this change? The NCSC believes this is a trick scammers are now using to filter out junk data from genuine user details. Anyone who recognises it as a phishing attempt and wants to outwit the scammer with a false username and password will usually only enter the password once. If they are asked to enter it twice, they are not likely to enter the same character string again – usually because they just entered a random combination of letters without thinking.
However, if a victim enters the same username and password twice, the scammer can presume they have not detected the phishing attempt and that the username/password combination is correct. This way, fraudsters can automatically sort out junk details from those more likely to be real.
Username verification
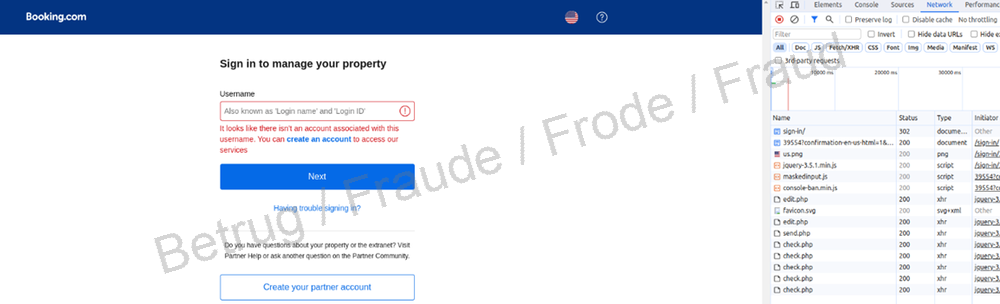
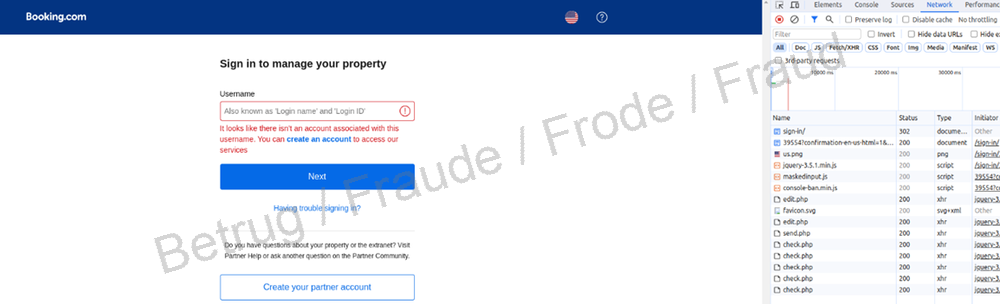
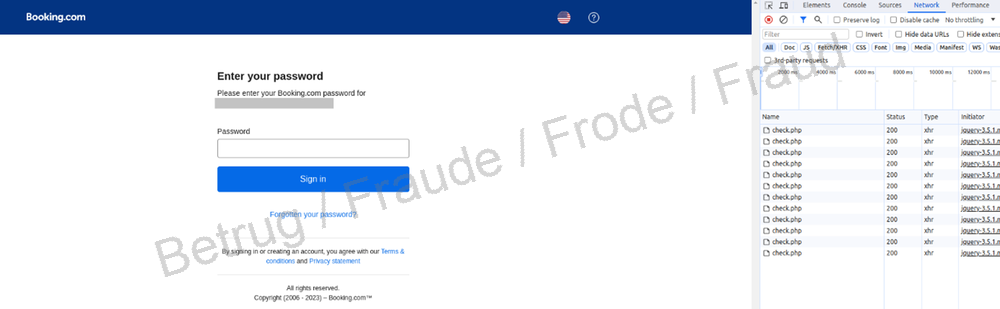
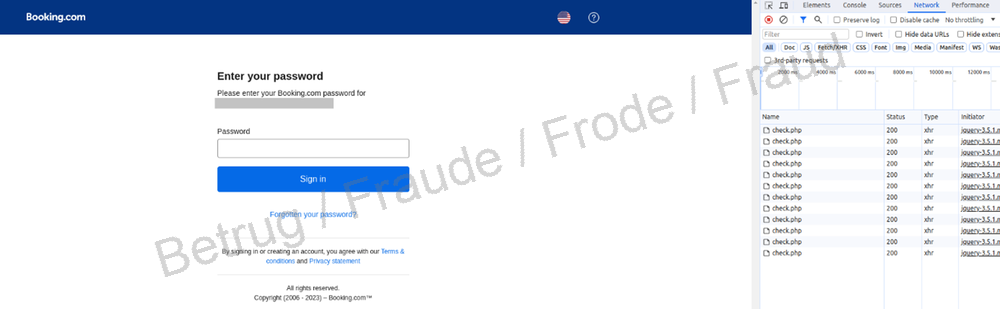
A new form of phishing targeting users of Booking.com goes one step further. If, on the phishing website, you enter a username that is not registered with Booking.com, you will not be asked for a password or any further details. But if the username is already registered with Booking.com, the victim will then be asked to enter their password.
On closer inspection it can be seen that the fake site is running a check script at regular intervals on the real Booking.com website to verify whether that username exists. It does this by trying to log in on the real website using the username entered on the fake site.
However, this method can only work if the username and password are entered in two separate steps, as is the case with Booking.com, and the website indicates after the first step that the username does not exist. This is why many websites have stopped performing user verification in two steps: instead, the username and password have to be entered at the same time. If either entry is incorrect, the website does not say whether it is the password or username (or even both). The user is only informed that login has failed. This leaves phishers no way of finding out whether the username exists without first trying it out themselves.
Recommendations
- Set up two-factor authentication whenever possible. This provides an extra layer of protection to prevent your account from being hacked.
- No bank or credit card company will ever ask you by email to change passwords or verify credit card details.
- Never enter personal data such as passwords or credit card details on a website you opened by clicking on a link in an email or text message.
- Bear in mind that email senders can easily be faked.
Current statistics
Last week's reports by category:
Last modification 30.01.2024