Mobile phones have become our permanent companions. These small, compact devices also contain more and more personal data, such as photos, contacts, emails and text messages. Therefore, the loss or theft of data can quickly result in serious consequences. In general, the same security rules apply as for a PC or notebook, except that a mobile phone's size makes it is easier to steal or lose. The NCSC has compiled nine practical tips to make your mobile phone more secure. The focus is on public WLAN use.
Nine practical tips for secure mobile phone use
- 1. Always lock your phone
- 2. Use public WiFi networks securely
- 3. Use an official app store
- 4. Install antivirus software
- 5. Install updates
- 6. Save your data regularly
- 7. Activate encryption on your device
- 8. Activate "Find My…" and have access to remote wipe
- 9. Use caution with public charging stations
1. Always lock your phone
People have their mobile devices with them whenever and wherever they go. But sometimes these devices are left behind and forgotten somewhere, e.g. during a lunch break, at the gym or on a train
In such cases, it is important that strangers be prevented from accessing the contents of the device. Losing information such as professional and personal emails, photos and phone numbers could be detrimental not only to you, but also to others if it ends up in the wrong hands.
Depending on the make and model of the device you use, the following methods are available:
- Digital fingerprint
- Face ID
- Iris recognition
- Password or PIN code
Be sure to enable such authentication methods. Make sure that your mobile phone locks itself as quickly as possible (30 seconds) after inactivity. Choose a sufficiently long and unique PIN code. Do not choose simple number sequences such as 123456 or 234567, nor numbers with a personal connection (e.g. date of birth, postcode, car registration number, etc.).
2. Use public WiFi networks securely
Public WiFi internet access points (hotspots) can be found at railway stations, airports, hotels, near public areas and places, and in bars and restaurants. The name of the WiFi network (SSID; service set identifier) usually ends in *_free, *_open or *_guest.
One of the biggest risks when using hotspots is directly related to how they work. Everyone can choose any name they want for their WiFi network. Imagine, for example, that you are in an airport terminal waiting to board your flight. You go in search of a WiFi network that the airport operator has made available so that passengers can access the internet.
You open the list of available WiFi networks and soon find a network called "WLAN_airport_free".

It seems to be one of the public WiFi hotspots provided by the airport for transit passengers.
When you log on to this official hotspot, there are security mechanisms that allow individual users to be protected from each other so that the network traffic cannot be intercepted (sniffed) by third parties. However, no one can guarantee that any of these mechanisms are active. If this is not the case, cybercriminals can read all the data you access via the internet, provided it is on the same network and the data is not encrypted, even passwords. In any event, fraudsters can see which websites you are visiting at any given time.
The name "WLAN_airport_free" that appears is not necessarily the airport's official hotspot. It could also be a network that is only pretending to be provided by the airport operator. For example, fraudsters can use a smartphone to generate a WiFi hotspot with exactly the same name as the airport's official hotspot. Generally, devices connect to the WiFi network with the highest signal strength first. Since the fraudster is only a few metres away from you and offers the strongest signal, your device will connect to the fraudster's network.
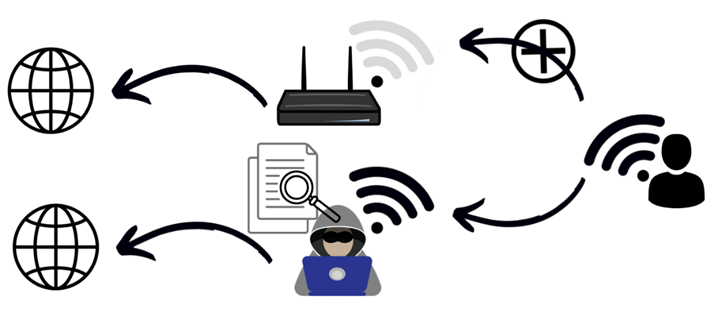
In addition, there are also WiFi services for which a fee is charged. This type of service is mostly offered in touristic city centres, where demand is the highest. A payment, usually by credit card, must be made when logging on to such a network. Fraudsters exploit this situation by again providing a bogus WiFi hotspot with the same or similar name and requesting credit card details when a victim connects.
Recommendations
There is always a certain risk when you connect to a third-party WiFi network, as you can never be 100% sure who is behind it. The risk starts as soon as the connection to the WiFi network is established. An attacker can make your device download malware already at this point, giving them access to all of your phone's data.
Another risk is that the person who set up the fraudulent WiFi network can read all the information you leave behind when you surf the internet. It is therefore important that your connection to any websites you visit be encrypted. When connecting via a public WiFi hotspot, never enter login credentials on websites that are not encrypted. Look for "https" in the URL or the padlock symbol in the address bar. You should generally refrain from using sensitive services such as e-banking and reading emails at public hotspots.
If in doubt, use your mobile phone network for data communication; when abroad, use the roaming function.
It is advisable to use a VPN service. In this way, all communication is "hidden" and an attacker has no chance of reading the navigation history or data. A VPN connection is absolutely essential for business use (e.g. business emails).
Deactivate WiFi and Bluetooth when you do not need these services. This helps to avoid attack methods that cybercriminals use to penetrate your device undetected. It also reduces battery consumption.o the public station.
3. Use an official app store
One of the most important attack vectors on mobile devices is the installation of malicious apps. On average, 200 million apps are installed on mobile devices every day, ranging from e-banking apps to shopping list managers. Not all apps are equally secure, however, and this applies especially to the source from which they are obtained and installed.
Aside from the app stores that are preinstalled on mobile phones by phone manufacturers (e.g. Google Play, Apple's App Store), other stores that offer apps also exist. These are called alternative or third-party app stores. While the official app store providers carry out in-depth checks on the apps, this is not the case with some alternative stores, or only to a limited extent. The NCSC therefore recommends downloading apps only from the official app stores. Only use alternative app stores if you are aware of the possible security problems and you trust the sources implicitly.
Read the reviews from other users and the app's general terms of use.
Another risk when installing apps is hidden in the access rights they ask you to grant. Avoid apps that require too many access rights. Only allow an app the rights it needs for its actual purpose.
- A weather app does not need access to telephone contacts.
- A shopping list app does not need access to photos.
4. Install antivirus software
Just like viruses that attack your PC, there are also viruses that target mobile phones. Therefore, you should set up antivirus software on your mobile device too.
5. Install updates
The updates published by manufacturers and developers not only offer new functions, they also help to resolve vulnerabilities and prevent programming errors. It is therefore important to always keep your device and all apps installed on it up to date.
6. Save your data regularly
The NCSC recommends that you regularly save the data on your device, be it via a cloud service or syncing to your PC or directly to an external storage device.
An accident, loss or theft can happen quickly!
7. Activate encryption on your device
In the event of loss or theft, encryption ensures that the confidential data on your device cannot be accessed by unauthorised third parties. Nowadays, encryption is automatically enabled on many devices, provided the mobile phone is protected by a PIN, Touch ID or Face ID. However, it is worth checking whether encryption is enabled, especially with older devices.
8. Activate "Find My…" and have access to remote wipe
Leaving your mobile phone somewhere can happen before you know it. To counter this problem, many phone brands offer a remote device location tracking service.
- On Android, the service is called "Find My Device" and can be downloaded directly from the official Play Store.
More information on how to activate it and how it works can be found in the Google Account Help.
- On Apple, the app is called "Find My" and is installed as standard on each Apple device. However, it must be manually activated. More information on how to activate it and how it works can be found in the iCloud User Guide.
- On Samsung, the function is called "Find My Mobile". It is likewise installed as standard on devices and also requires manual activation to work. More information on how to activate it and how it works can be found und Find My Phone
Generally, these smartphone location tracking functions require devices to be switched on, connected to a WiFi network or have mobile data activated, and have location sharing enabled.
If this is the case, devices will be able to transmit their exact location and receive instructions such as to wipe themselves, play a ringtone, etc.
In addition, some device models can be configured so that the data they contain is automatically deleted after a certain number of failed password attempts.
9. Use caution with public charging stations
As soon as you connect your device to any USB port to charge it, there is a certain risk that data can be accessed. It is possible that information about the type, brand and model of the device will be read during the charging process. However, it is also possible that malware could be installed.
The best way to protect yourself against this is to use only the power adapter supplied with the device when charging it in public places.
An external battery (power bank) is also a good solution. This means you can charge the external battery at a public station and then charge the mobile phone from this battery. In this way, the phone is never directly connected to the public station.
Last modification 17.03.2025





