25.01.2022 - The number of reports received by the NCSC remained high last week. Fake extortion emails supposedly in the name of prosecution authorities dominated again, accounting for almost 35% of the reports. In addition, the NCSC received reports of phishing emails which at first glance appeared to have been sent in a very targeted manner. CEO fraud is increasingly personalised and a giveaway promotion purportedly from NASA promised that amounts paid in would be instantly doubled.

Targeted phishing?
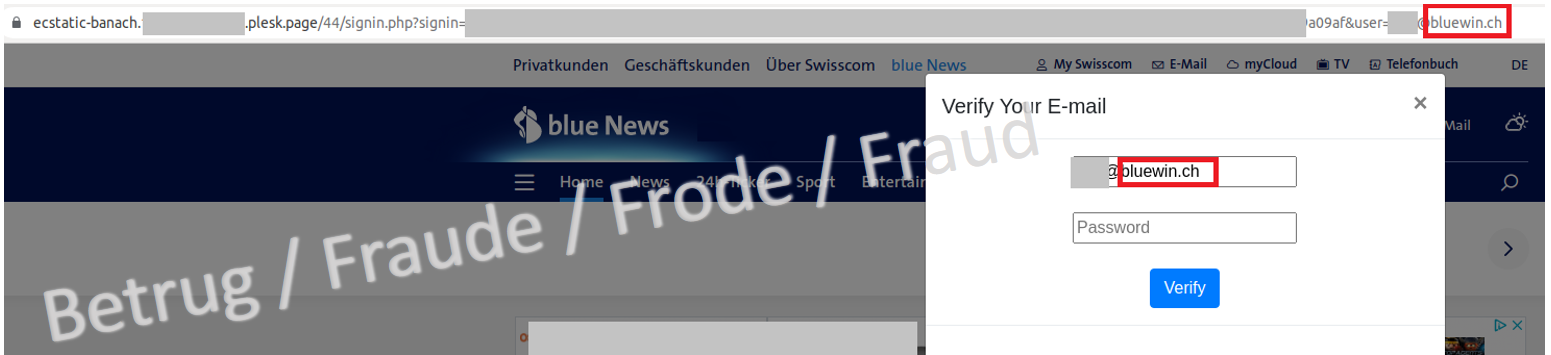
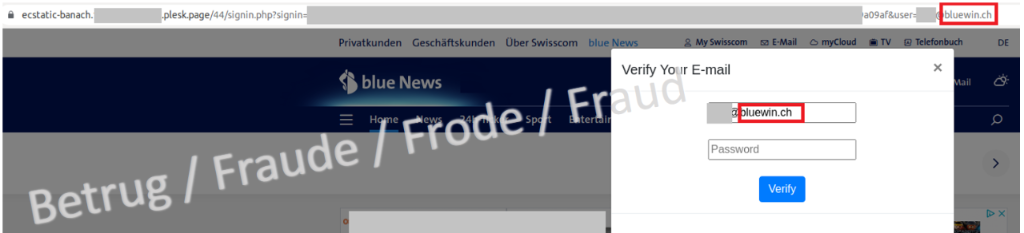
Last week, the NCSC received a report from a company that at first glance appeared to concern a very targeted phishing attempt. The attackers tried to obtain an employee's email account credentials. A pop-up login window which requested the user name and password was displayed in the foreground, and the company's website was greyed out in the background. As phishing attempts are usually a mass business, such a targeted attempt is rather unusual. The alarm bells rang because this attempt indicated a targeted attack on the company.
However, it quickly became apparent that the phishing link contained the email address. If this email address was replaced and the email address of an email provider was entered, for example, the greyed-out page in the background changed and the homepage of the corresponding email provider was displayed. The phishing attack was not targeted; instead, a short hidden script recognised the recipient's email address domain, loaded the website page of this domain in the background and then displayed it. Although the attackers send these emails to random email recipients, the phishing page always gives the impression of being very targeted.
Email accounts are particularly lucrative for attackers, as email addresses are the key to a multitude of online services. For example, users can request a password reset link from most internet services, and this is then sent to their email address. This link can be used by an attacker to gain access to the internet service. This means that, if an attacker has the credentials for an email account, he or she also has indirect access to various internet services. It is no wonder that such access credentials are particularly popular with attackers.
- Install two-factor authentication whenever possible. This offers an additional layer of protection to prevent your account from being hacked, especially if the attackers have access to your email account.
- Never divulge personal data such as passwords or credit card details on a website that you accessed by clicking on a link in an email or text message.
CEO fraud: targeted attacks, including a case involving a WhatsApp account with a profile picture
CEO fraud is frequently reported to the NCSC. Typically, the attackers systematically search public company websites for names and email addresses of CEOs and those in charge of the finance division. If the attackers find what they are looking for, a fake email ostensibly from the CEO is sent to the finance division and an urgent payment instruction is issued. The texts used are very generic and mostly identical. Until now, fraudsters have not made much effort to specifically address victims and personalise their requests accordingly.
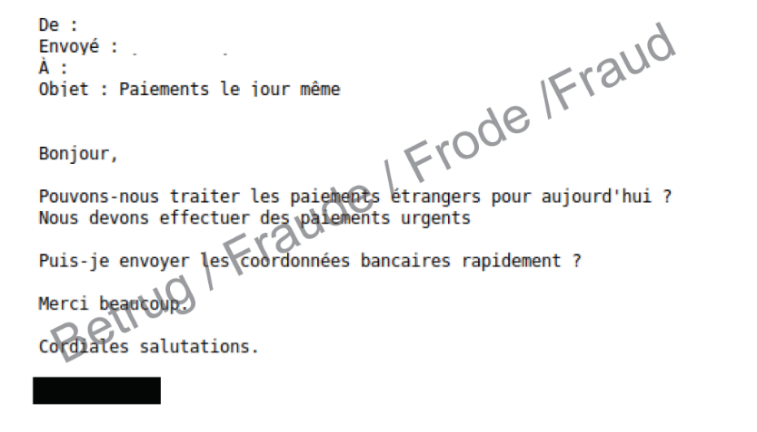
However, in two reports received by the NCSC last week, significantly more effort was made and the attacks were tailored to the victims. In one case, the fraudsters created a fake WhatsApp profile for the CEO in advance. They used a screenshot from a promotional video for the company as the profile picture.
In another case, which was directed against a sports club, the purported president asked the treasurer if he could pay an invoice for sports shoes. Again, the fraudsters found out information about the club in advance and adapted the scam to the victim.
- Raise all employees' awareness of CEO fraud! Especially employees in finance divisions and in key positions must be informed about these possible methods of attack.
- In the case of associations, all presiding members and treasurers must receive training.
NASA giveaway
The NCSC already reported on giveaway campaigns in Weekly review 33. Such offers sound tempting: if money is paid into a specific cryptowallet address, double the amount will be paid back. The potential victims are put under pressure by a time counter indicating that the offer is only valid for a short time, or that the available amount will soon run out. This week, the NCSC was notified of another such scheme. This time, in order to give the offer a serious look, planet earth was not enough. The victims were made to believe that NASA was behind the campaign and the name of the former astronaut Bill Nelson was misused by the fraudsters to inspire even more confidence in the victim.
For some time now, other made-up stories have also been observed in this context. For example, there is a version with Elon Musk which likewise promises that amounts paid in will be doubled.
- Ignore such promotional campaigns: generally, the greater the promised return, the higher the risk.
- Never allow yourself to be put under pressure.
Current statistics
Last week's reports by category:
Last modification 25.01.2022