16.08.2022 - The number of reports received by the NCSC rose slightly. In a hacker attack against an online shop user's account details, an attempt was made to disguise the attack by email bombing. The new type of phishing attack using QR code bills described in the last weekly review is already being used by phishers on a large scale and in different forms.

Attackers hide attack in an avalanche of emails
Last Wednesday, shortly after midnight, hundreds of emails flooded the inbox of an individual who then reported the attack to the NCSC. Almost all of the emails were registration confirmations from various portals for online services and webshops which had never been requested. However, among the approximately 1,500 notifications received, two emails which referred to a webshop account that the victim actually uses were hidden. These were notifications from a Swiss webshop that an order had been placed and that the contact details had been changed. They also stated that the victim should contact the company if these changes had not been made by him. It appears that the hackers succeeded in gaining access to the victim's account, changing the postal address, email address and telephone details, and placing orders to the tune of CHF 1,800.
The email bombing with the registration emails appears to have been done to disguise the actual attack. Despite the avalanche of emails, the victim looked through the emails, recognised the attempted attack, reacted quickly and was thus able regain control of his account and cancel the orders. The flood of emails eased immediately after the victim recovered control of his account.
It is not known how the attackers obtained the victim's access details. It can be assumed that the ordered goods would have been delivered to a letterbox from which middlemen would have collected the goods.
- Always use a separate password for each online service.
- Use multi-factor authentication whenever possible.
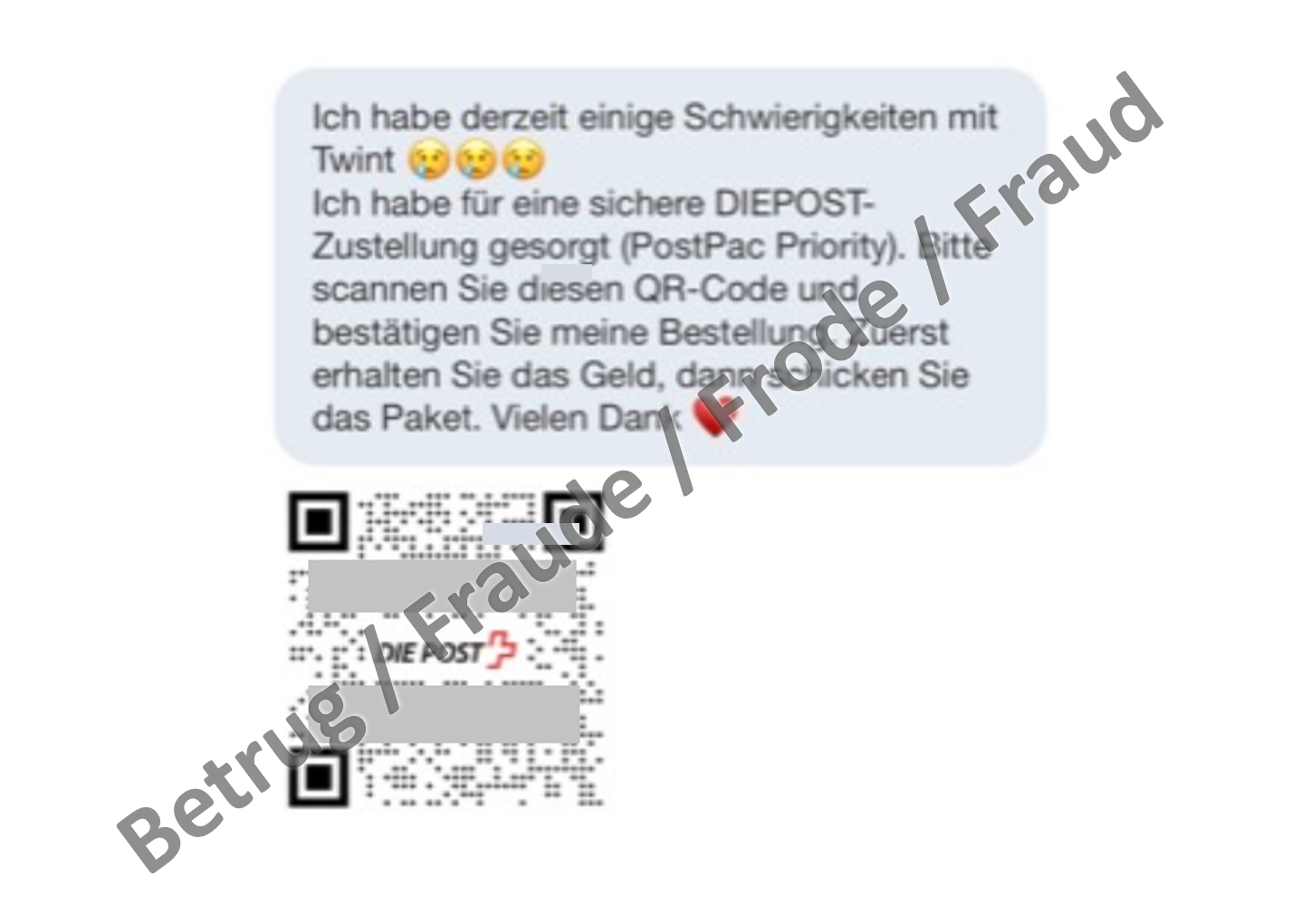
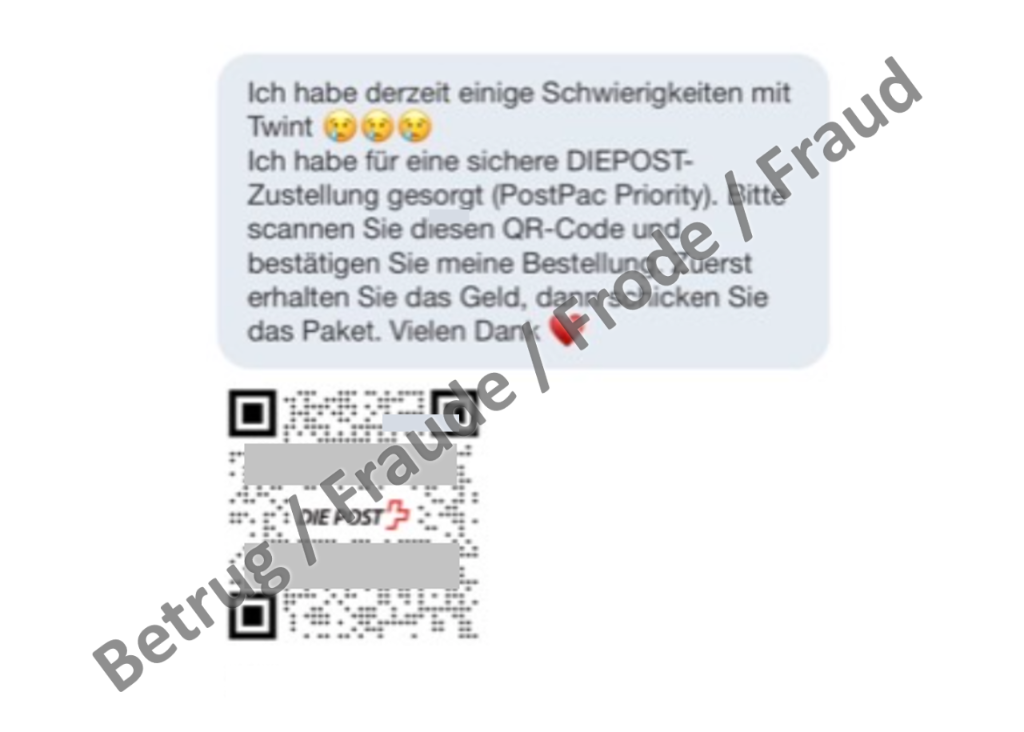
Phishing with QR code bills continues to gain ground
Last week, the NCSC reported the first cases of phishing with a QR code bill and suspected that this was an initial trial run by the fraudsters. However, in the meantime, reports of phishing attacks in which the links are embedded in QR codes are increasing. In particular, phishing attempts in connection with classified ads are increasingly being carried out using QR codes.
Bills with QR codes should definitely be checked more closely before scanning the code. Especially if the bill is unexpected or another form of payment was previously used.
Here again are the measures suggested last week:
- Use a reliable app that is recognised as secure to scan QR codes.
- After scanning and before execution, most scanners will display the action to be performed or the page to be accessed. Check this information.
- Never enter login credentials on a website that you accessed via a QR code.
- You can find more background information on QR codes here:
QR codes – uses and risks
Current statistics
Last week's reports by category:
Last modification 16.08.2022