17.10.2022 - The number of reports received by the NCSC was higher last week. Several interesting phishing attempts to obtain Office 365 access credentials were reported to the NCSC last week. In one case, an HTML file was attached to the phishing email instead of a phishing link. In another, the fraudulent link was embedded in a QR code. Furthermore, the NCSC also received reports of phishing attempts targeting SBB, in which the phishers tried to steal the SwissPass or SwissID access credentials.

Two new methods to obtain Office 365 credentials
Office 365 credentials are of great interest to attackers, as this account can usually be used to attack other services of the same person in addition. Therefore, it is no wonder that phishers pull out all the stops to get hold of this data. Last week, two previously unknown methods were observed.
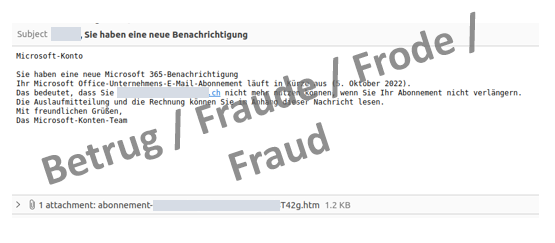
Several reports concerned phishing emails which contained an HTML document (recognisable by the file extension ".htm") as an attachment.
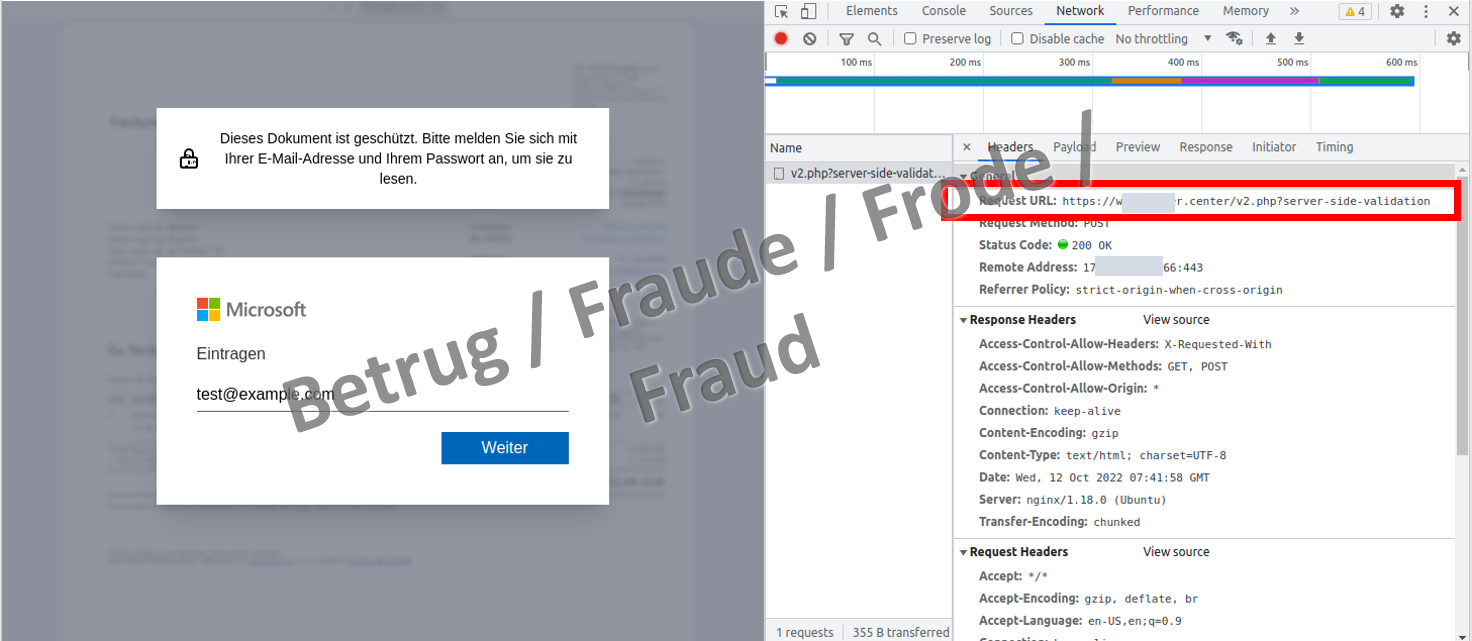
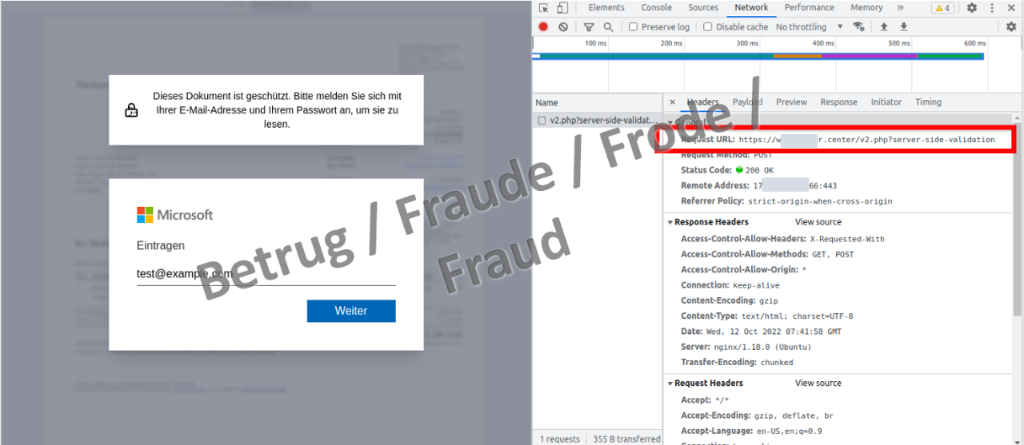
The partly automatic execution of the HTML code displays a Microsoft Office 365 login screen. The username and password are then sent to the phishing domain.
The phishing page was opened in the browser window for the NCSC's analysis. The following image shows that the phishers reserved a separate domain for the scam.
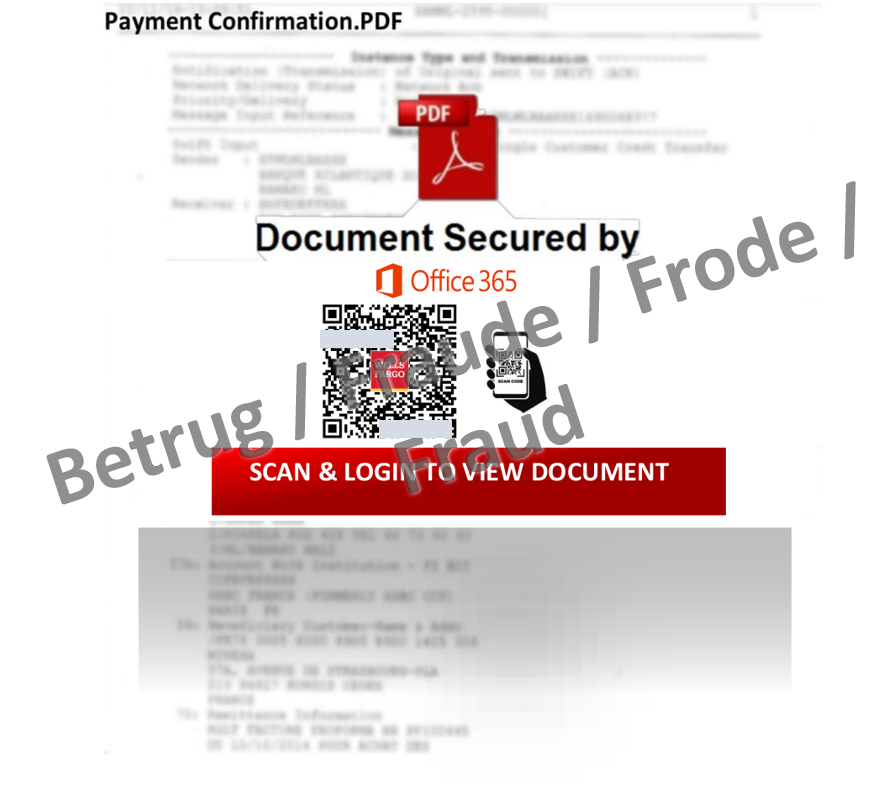
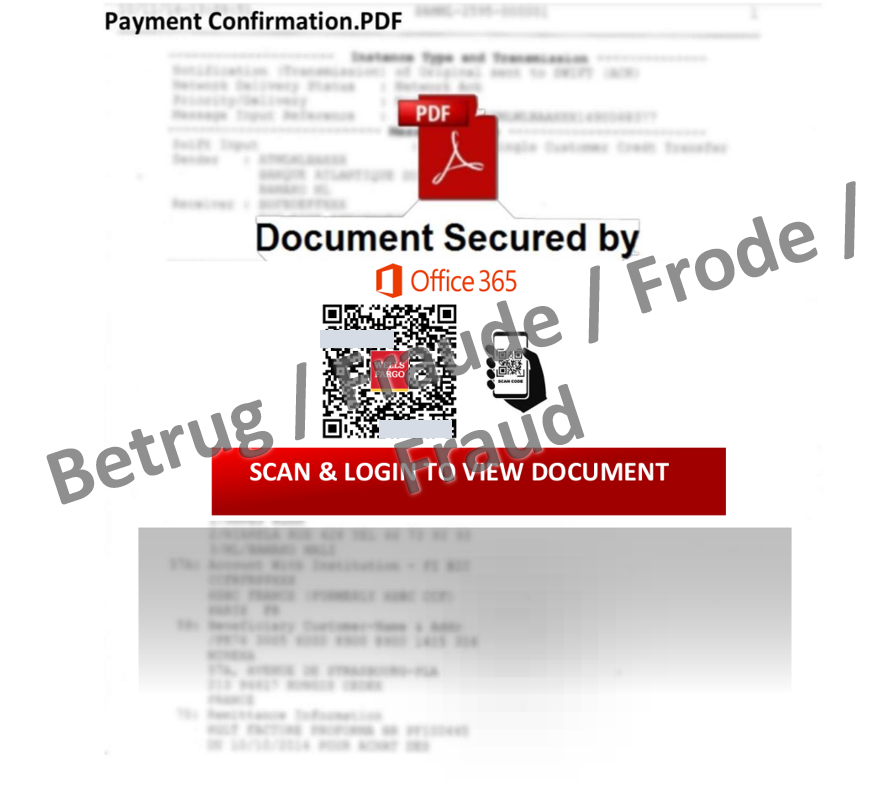
A different approach in order to obtain Office 365 login credentials can be seen in another case. The phishers posed as the financial services company Wells Fargo and claimed that a payment had been triggered. Attached to the email was a PDF named "Wellsfargo_ACHCOPY.pdf" in which a QR code was displayed on an image, again with a blurred invoice in the background.
Scanning the QR code leads to a fake Microsoft Office 365 phishing website, which in turn attempts to steal the login credentials.
It is safe to assume that both methods are designed to camouflage the link to the phishing page a little better.
Phishing mail in the name of SBB requires SwissPass and SwissID login credentials
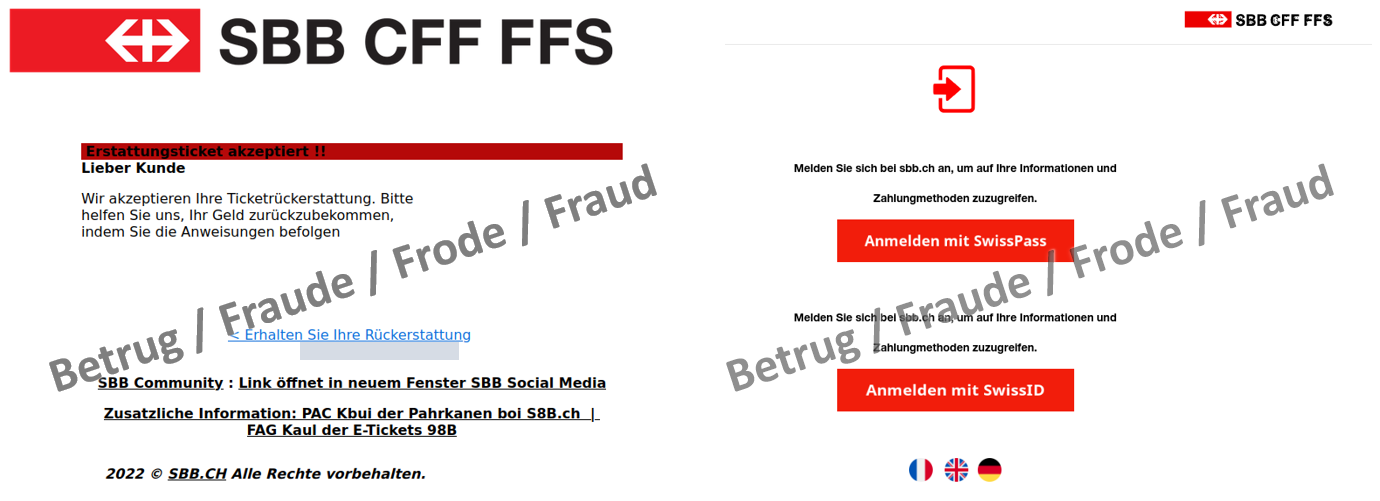
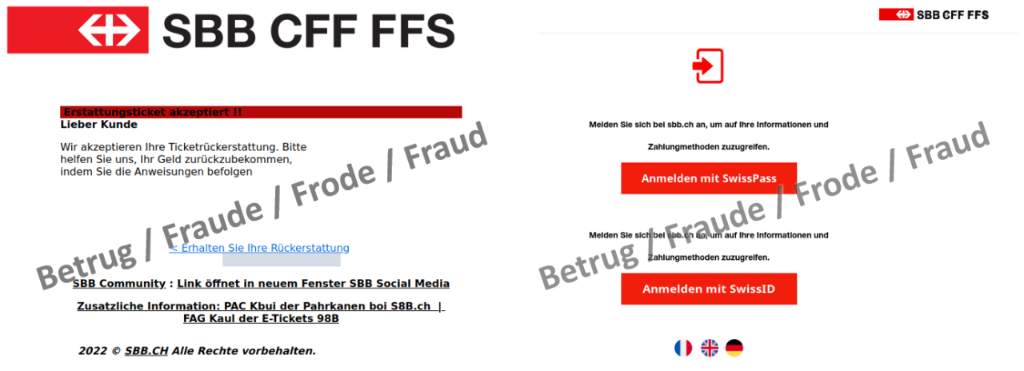
Another phishing email was allegedly sent in the name of SBB. The embedded link for the supposed refund leads to a login window where the SwissPass or SwissID access credentials are phished.
A somewhat cryptic text can be seen at the end of the email. It can be assumed that this came about when a blurred image was scanned by machine and was not corrected afterwards.
- Use multi-factor authentication whenever possible. This is sometimes called two-factor authentication or multi-/two-step verification.
- Do not click on any links in emails if you cannot identify their origin beyond doubt.
- Do not enter Office 365 login credentials based on a link in an email. Instead, go to your Office 365 homepage in the browser and log in there. This applies likewise to all other login processes.
- Use the reporting form to report any such attempted attacks to the NCSC.
Current statistics
Last week's reports by category:
Last modification 17.10.2022