25.04.2023 - Every additional app poses a potential security risk. So any apps that you are no longer using should be deleted. The fewer apps you have, the easier it is to keep track of them, resulting in a lower security risk. Permission is requested when an app is used for the first time, and sometimes for updates. Many apps access personal data. An unusual example reported to the NCSC shows that these permissions can also be exploited and abused.

When a colleague recommends an app
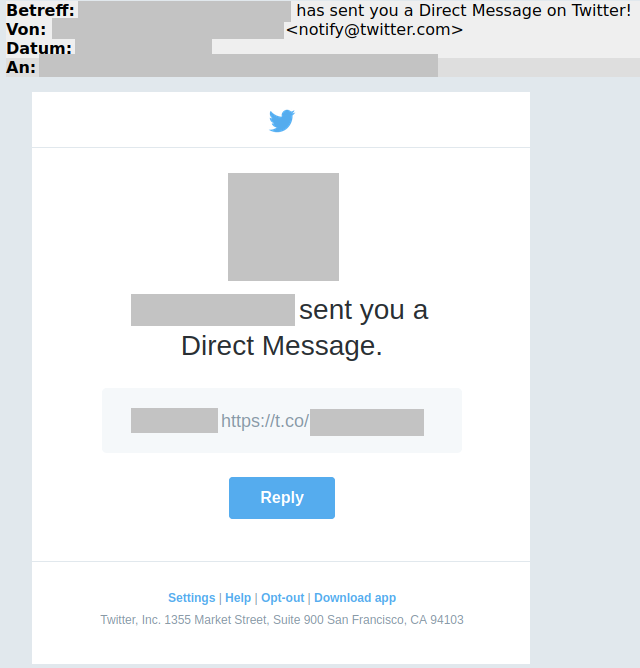
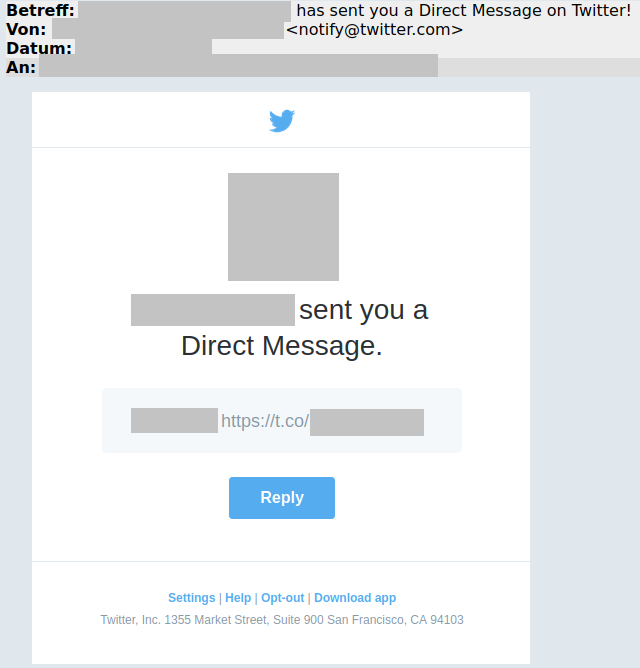
In this case, it all started with an innocuous direct message via Twitter that the person reporting received from a colleague. On the face of it, the message seems unsuspicious: it was sent via Twitter and actually originated from the colleague's account.
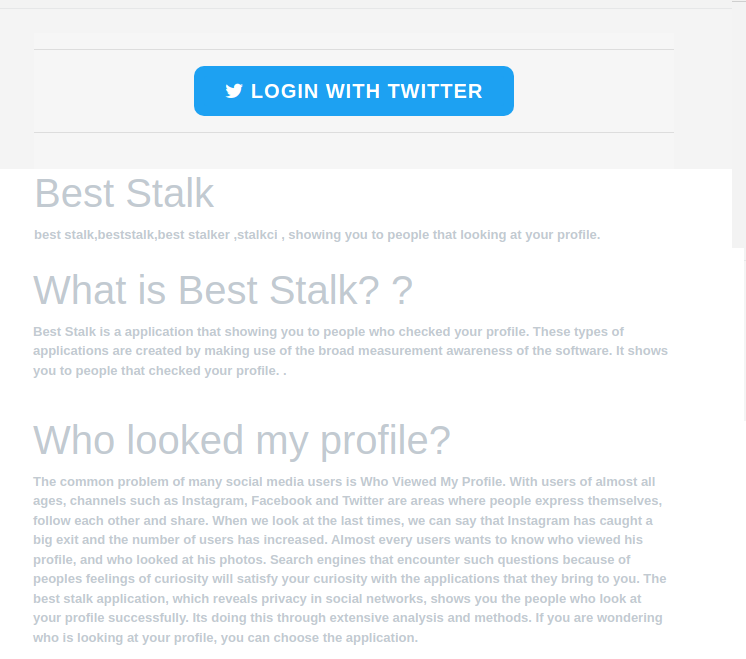
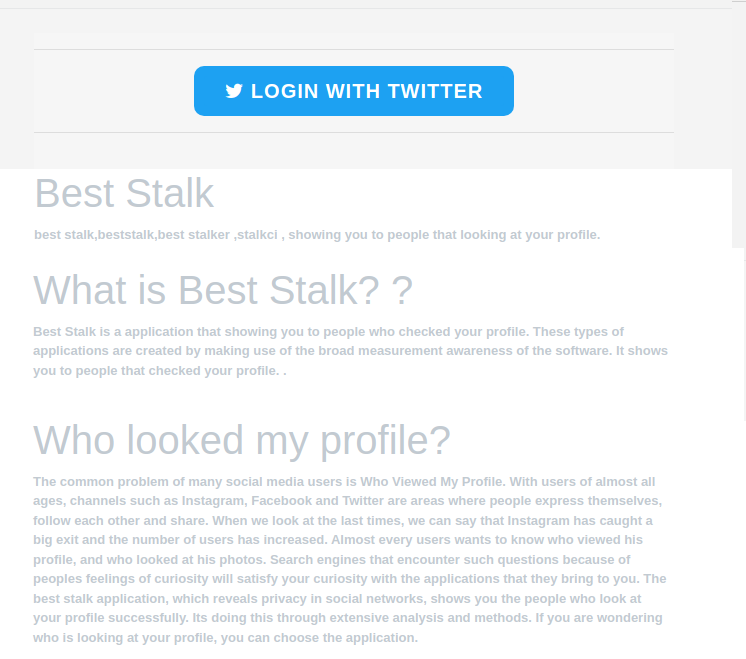
However, clicking on the link opens a dubious page that prompts the visitor to log into Twitter in order to install an app called Best Stalk. This app claims that it will show you the people who viewed your profile on Twitter, Facebook and Instagram. The procedure is simple. All you need to do is share the necessary data so that the app can search your Twitter account.
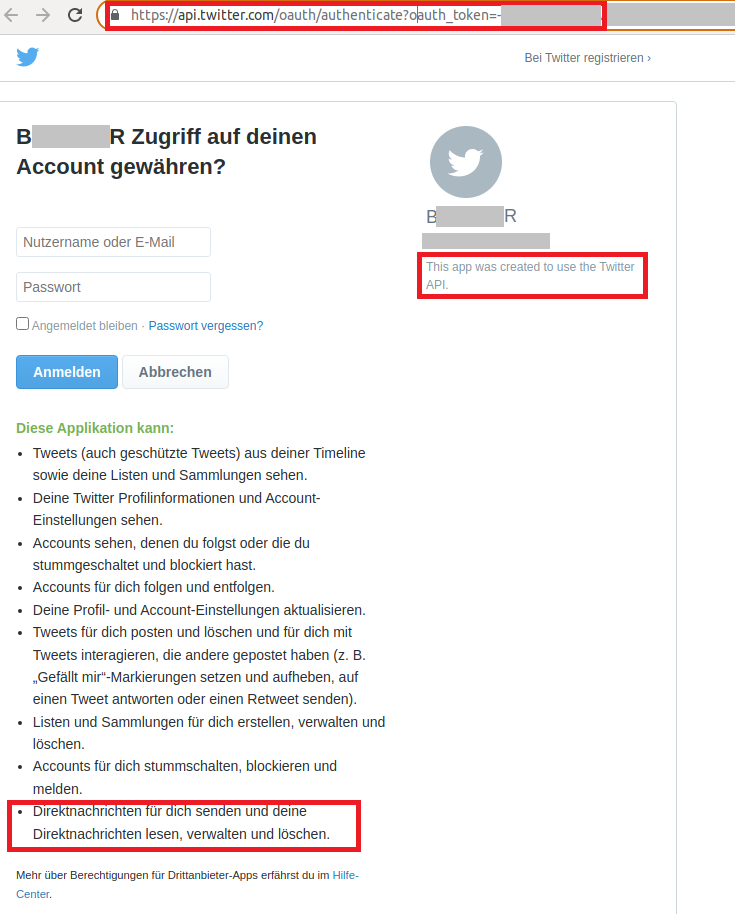
The username and password for the Twitter account are then to be entered on the next page. This could be a classic example of a phishing site. Surprisingly, though, a quick check of the address bar shows that the address actually belongs to Twitter. Nevertheless, it also becomes clear that this procedure gives the supposed app developer full access to the user's entire Twitter account. The rights that are supposed to be granted include:
- View Twitter profile information and account settings
- Follow and unfollow accounts
- Update profile and account settings
- Post and delete tweets and react to tweets posted by others
- Create, manage and delete lists and collections
- Send direct messages and read, manage and delete direct messages
The third party can then do virtually the same things as the account owner. It is even possible to send direct messages as a result. This also explains how come the person who reported the case received a genuine message from his colleague, who fell for precisely this procedure earlier on and entered his user details. This meant that his account could then be used to send a direct message to all contacts.
Bug or feature?
But how is it possible for such a dubious site to hide behind an official Twitter address? This is due to application programming interfaces (APIs). On Twitter, application developers can use this interface to access Twitter data and thus create their own "Twitter app". A well-known example is Tweetbot, a third-party application for the Twitter social network. All developers can easily and immediately register their own application and thus gain access to the Twitter interface. By default, however, such applications can only access public information. Certain functions, such as sending direct messages, require additional authorisation, and this is where the aforementioned website comes into play. By providing a username and password, you give Twitter permission for what in this case is a rogue developer to access your Twitter account via the interface.
Recommendations:
- Only install trustworthy apps by using reviews to check.
- Give apps only the rights they absolutely need.
- Any apps that you are no longer using should be deleted.
Factsheet on using apps
The Federal Administration has produced a factsheet to raise employee awareness concerning the use of apps and especially social media apps. However, the tips and advice also apply for users outside the Federal Administration.
Notice:
The document contains links to information that is only available on the intranet.
However, further information can also be found at:
Current statistics
Last week's reports by category:
Last modification 25.04.2023