22.08.2023 - Phishing attacks on Office365 are increasingly in the form of man-in-the-middle attacks, with the attacker slipping in unnoticed between two parties involved in an exchange. In this way, content can be changed in a network connection that is actually protected. What is so perfidious is that the current variants of these attacks are almost undetectable, as the attackers' valid certificates are displayed in the browser.

The NCSC has already reported several times on phishing attacks on Office365 accounts. Initially, such phishing was limited to stealing usernames and passwords. With the widespread use of two-factor authentication, attackers began to exploit this method as well. They harvest usernames and passwords in the first step, and enter these on the genuine website, triggering the prompt for the second factor. This is when the attackers interfere with the communication by inserting a prepared website on which the second factor is entered. (For real-time phishing, see Week 6: Real-time phishing of secured Office365 accounts. This requires the attackers to input the data promptly on the correct page, which requires human interaction and is therefore quite laborious. This procedure is referred to as a man-in-the-middle (MiTM) attack.
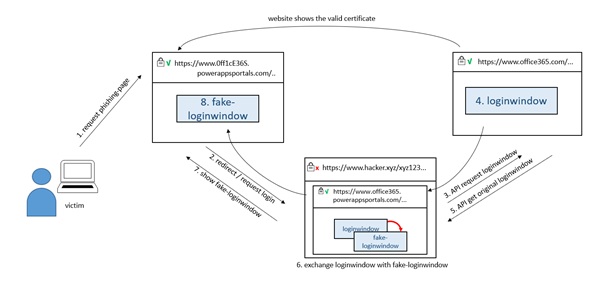
To reduce the work involved, the attackers try to automate this process. In the traditional variant, attackers place a server, a so-called proxy, between themselves and the victim. Instead of the victim communicating directly with Microsoft, the server intercepts the data, decrypts it and then forwards it to Microsoft. The request for the second factor can in turn be sent to the victim. The victim's response is again intercepted by the server and the attackers can hijack the session. However, there is a major disadvantage with this method of attack. Although the address bar contains the correct URL, the victim communicates with the wrong server (proxy), which inevitably leads to a certificate error.
The use of website certificates meant that it was easy to detect these attacks until recently. The browsers either displayed a warning themselves or prevented access altogether.
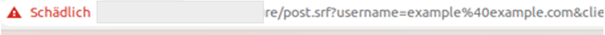
Recently, the NCSC has received several reports that these phishing attacks are using legitimate and valid Microsoft certificates, which means that no warnings are appearing.
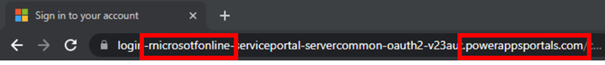
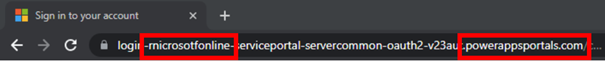
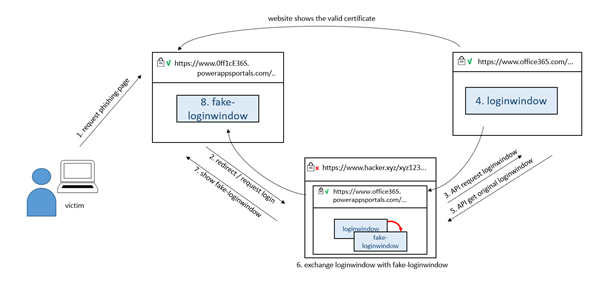
The website powerappsportals.com has a valid certificate provided by Microsoft and enables developers to provide their own automation solutions. This also includes direct access to the Office365 login procedure by means of an interface made available by Microsoft (so-called API interface). Using this interface, the hackers can retrieve the original login window entirely automatically and replace it with a fake login window, for example. In this way, they can switch the login window and harvest the contents (username, password, one-time token) and, unlike with the proxy variant, do so without the certificates being flagged as invalid.
Although carrying out an attack of this kind is complex and requires a certain amount of knowledge about the technology used, the access gained is obviously valuable enough to make the effort worthwhile.
Recommendations:
- Never enter a password or credit card number on a page you reached via a link in a message. It is most likely a phishing attempt;
- Check any website requesting your login credentials very carefully. Two-factor authentication does not protect you from real-time phishing.
Current statistics
Last week's reports by category:
Last modification 22.08.2023