24.10.2023 - After a short respite, the NCSC has again received several reports of malicious emails in the last two weeks that use old emails to trick the recipients into believing that they had already been in contact with each other. Since both the email sender and the old message seem familiar to the victim, the likelihood increases that the victim will click on the link and malware, in this case DarkGate, will be installed on the device. DarkGate is a downloader with advanced functions and also a door opener for ransomware.

The approach of using old email correspondence is not new. It is worth remembering Emotet malware, which already used this method, known as dynamite phishing, back in 2019 to trick its victims into opening a document. It did this by scouring the victims' Outlook file on infected devices. In each case, existing correspondence was used to send the malware to further potential victims. Since the recipient was aware of the old email, it was more likely that they would open the malicious attachment.
After the Emotet network was temporarily disabled by the prosecution authorities in early 2021, Qakbot malware adopted the old email trick. Qakbot had already been around for more than ten years at this point, but was overshadowed by Emotet and was also spread at times via the Emotet network as an additional optional malware module. Interestingly, the Qakbot authors had already implemented an "email collector module" in the summer of 2020, which extracted emails from the victims' Microsoft Outlook client using stolen access data, uploaded them to a remote server and then used them for further attacks.
In August 2023, Qakbot met the same fate as Emotet. Prosecution authorities in the United States and Europe managed to take over the botnet's command and control infrastructure. This meant that the attackers were no longer able to control the PCs they had infected. However, it seems that those behind it were not caught and the spam infrastructure was only partially dismantled.
For a few weeks now, DarkGate has been the next malware in the limelight to master the old email trick. In this case, a PDF containing a link to the malware is attached to the spam email.
DarkGate has been active since 2017. However, the malware only really came to light this summer after the purported developer boasted about new functions. These go far beyond the functions of an actual downloader. Among other things, it contains hidden remote access, a reverse proxy and a Discord token stealer, and is capable of stealing browser history. It can be assumed that criminal groups that previously tried to achieve their goals using Qakbot have now switched to DarkGate.
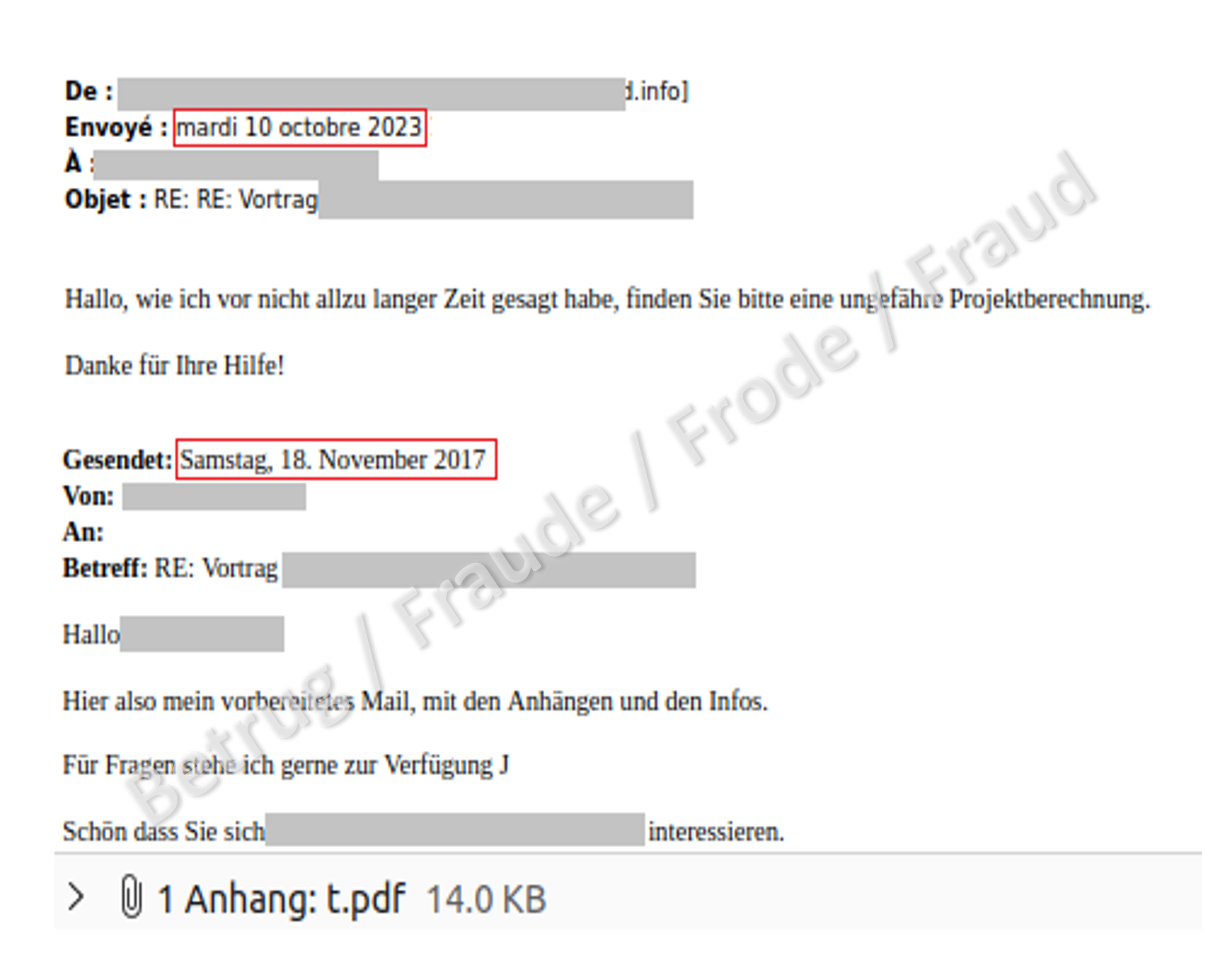
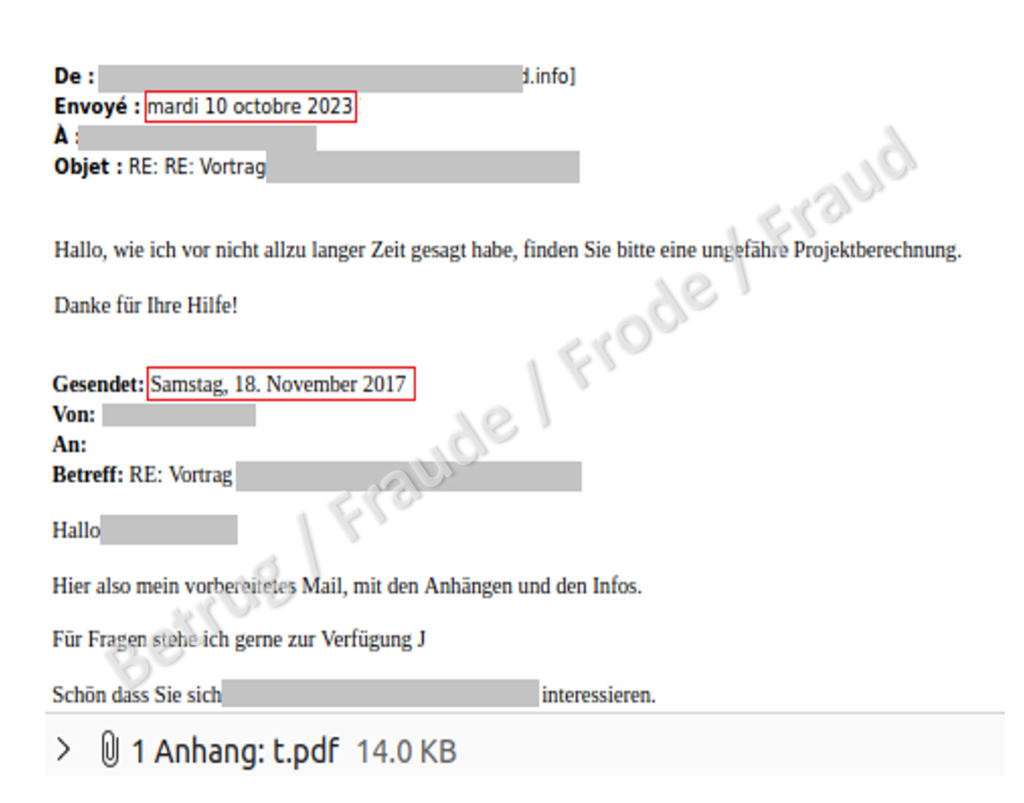
What is striking about the latest variants is that some of the correspondence is very old; in the case below, it dates back to 2017. Therefore, it cannot be assumed that the malware is currently actively intercepting email correspondence, but it is using emails from databases that were already stolen years ago by other players.
Skype and Teams also used for spreading malware
According to a report by the security service provider Trend Micro, DarkGate also uses other means of communication and is spread via compromised Skype and Microsoft Teams accounts, for example. Similar to the email approach, the compromised Skype account is known to the victim and had previously had contact with them. The message claims to contain a PDF file, but in reality it is a malicious VBScript (Visual Basic Script). This then attempts to download and install the malware.
The NCSC recommends the following tips to prevent infection with malware:
- Malicious emails can also come from known senders.
- Be careful if previous messages are suddenly resent out of context.
- Be careful when opening email attachments, even if they come from a supposedly trustworthy source.
Current statistics
Last week's reports by category:
Last modification 24.10.2023