07.03.2023 - The number of reports received by the NCSC increased again in the ninth week of 2023, with 871 reports, the highest number received this year and the fourth highest in its history. Threatening emails purportedly from authorities accusing the recipient of a criminal offence accounted for the largest share. Now, the NCSC is often being given as the sender of these scam emails. Reports of phishing have also increased in the last three months. This week, a case of real-time phishing was discovered, which seeks to exploit second-factor authentication.

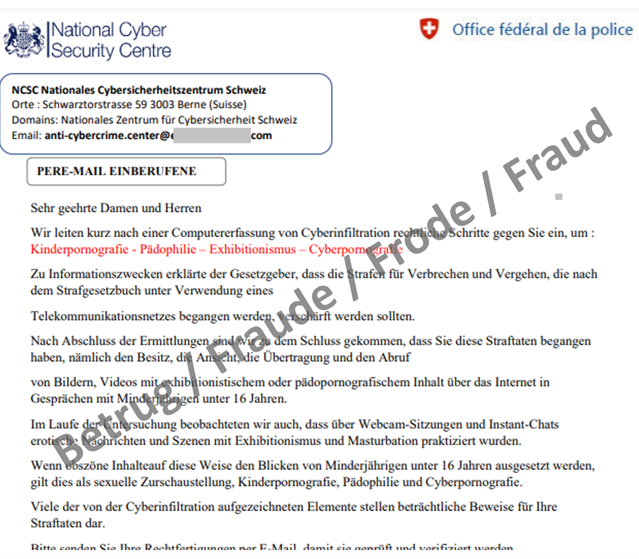
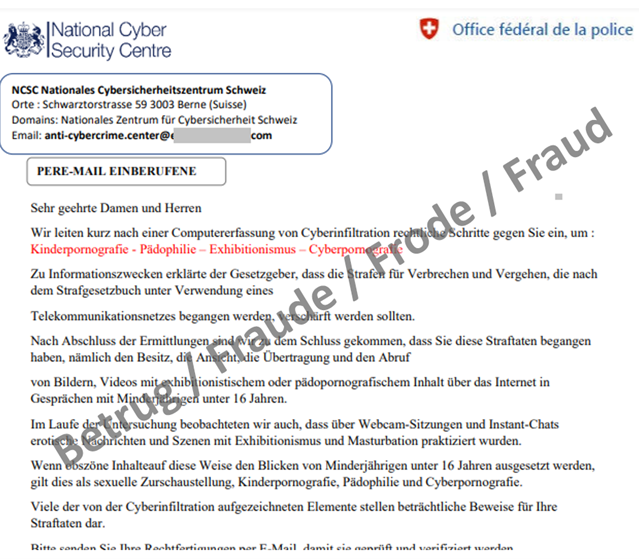
Numerous fake extortion emails also supposedly sent by the NCSC
Threatening emails purportedly from authorities accusing the recipient of a criminal offence related to child pornography were again reported in large numbers last week. Almost 40% (345) of the reports received were due to this phenomenon. It is no longer only prosecution authorities that are used as the email senders: a large proportion is now being sent in the name of the NCSC. In these cases, the attackers use the correct NCSC name, but the logo is taken from our colleagues at the UK National Cyber Security Centre.
As citizens regularly send us such emails, the NCSC receives a lot of feedback from concerned individuals via email and the reporting form. We would like to emphasise that neither the NCSC nor the prosecution authorities send information on ongoing proceedings via email. Any such emails are bogus. Ignore such fake extortion emails and do not allow yourself to be intimidated.
Real-time phishing attacks on Swiss banks
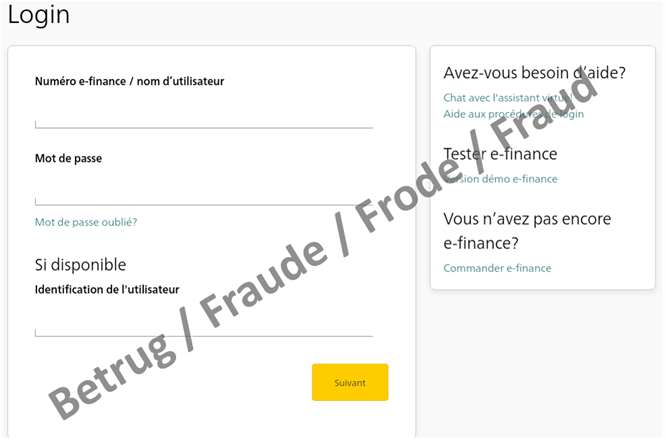
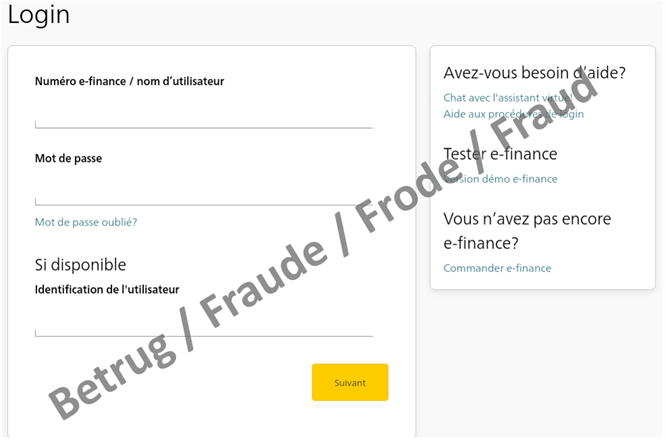
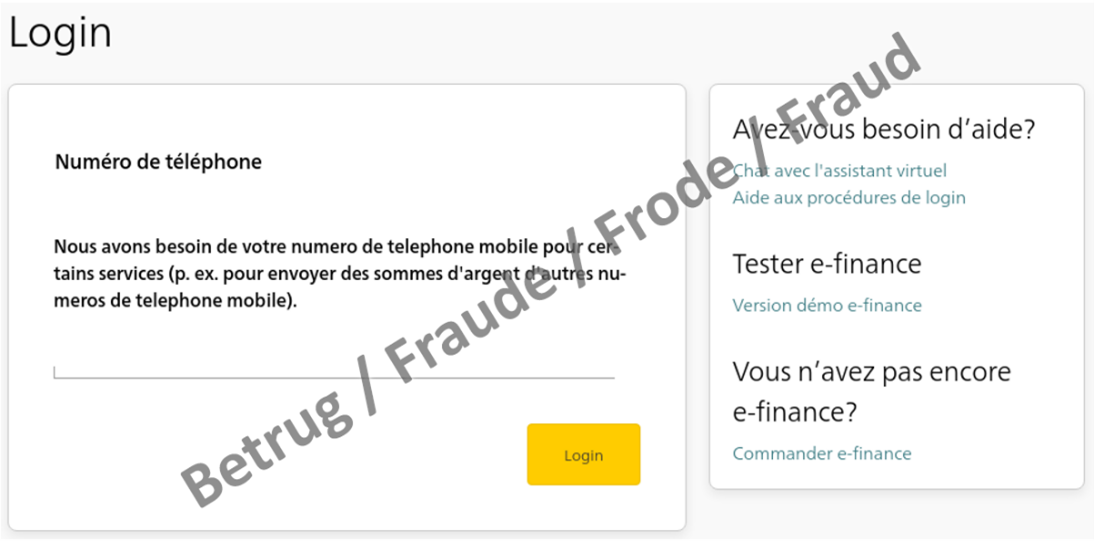
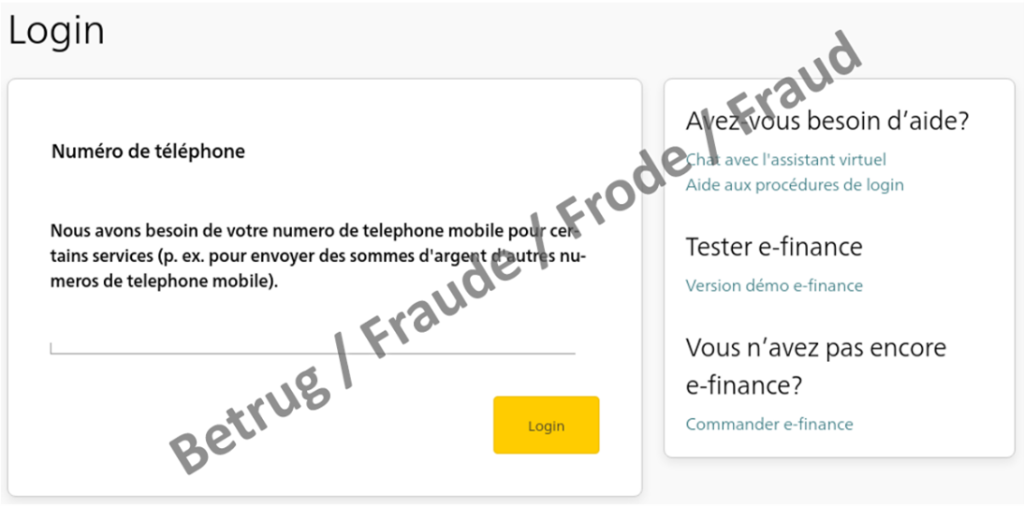
In the last three months, reports of phishing attempts have been steadily increasing. While in December 2022, the NCSC received 434 reports in the phishing category via its reporting form, in January 2023 this number had already risen to 541 reports, and in February the figure rose again to 676. As mentioned in last week's review, numerous new phishing variants are in circulation and the attackers are testing various variants. Last week, the NCSC primarily observed well-known real-time phishing attempts against financial institutions. In contrast to most phishing attempts, these cases did not involve credit card details; instead, they concerned access to online banking accounts. To do this, the attackers need to obtain the second factor, i.e. the one-time password, in addition to the username and password.
This phishing variant also starts with a request for the victim's "username" and "password" on a classical phishing page. However, at the same time in the background, the attackers use these credentials to log into the victim's account on the real online banking page. During this time, the victim is made to wait in a queue and is led to believe that the page is loading.
Once the username and password have been entered, a number – the "challenge" – is displayed on the online banking portal, and this has to be entered into a card reader. The second factor can be generated solely with the corresponding bank card and the card password, which in turn must be entered on the online banking page. Since the attackers are not in possession of the bank card, they have to get the victim to generate the second factor for them.
To do this, they hide the queue and reload the victim's phishing website where they publish the challenge they received when logging in, together with a request to enter the code into the card reader and then enter the result on the phishing page. If the victim also provides this code, the attackers can access the online banking account and initiate fraudulent payments. Finally, the attackers then ask for their mobile phone number. This allows them to communicate with the victim and to persuade them to provide the second factor at a later time or to make other rash moves.
How phishing emails fool the spam filter
The phishing email itself also contains a well-known trick. Additional text that is unrelated to the email is inserted under the actual phishing email. Whereas in previous cases the attackers inserted previous correspondence, in this case they made it easy and copied the Wikipedia entry for the city of Cologne. The attackers use this method to try to bypass spam filters. By inserting legitimate content, it is more likely that the fraudulent content will carry less weight in the spam rating.
Recommendations:
- Wherever possible, use two-factor authentication. This offers an additional layer of protection to prevent your account from being hacked.
- No bank or credit card company will ever send you an email requesting that you change your password or verify your credit card details.
- Never divulge personal data such as passwords or credit card details on a website that you have accessed by clicking on a link in an email or text message.
- Bear in mind that email sender IDs can easily be spoofed.
- Be sceptical if you receive emails that require action from you and otherwise threaten with consequences (loss of money, criminal charges or legal proceedings, account or card blocking, missed opportunity, misfortune).
Current statistics
Last week's reports by category:
Last modification 07.03.2023