01.02.2022 - Despite the decrease in reports of fake extortion emails, the number of reports received by the NCSC last week remained stable at a high level. The NCSC was particularly occupied with the zero-day vulnerability currently being exploited on QNAP NAS devices. Attention was also focused on a phishing email with a special attachment.

QNAP network-attached storage (NAS) devices currently at risk
Several reports on encrypted QNAP NAS devices show that the latest security vulnerability in these devices is being actively exploited. As this concerns a zero-day vulnerability, no current software update was available for this security vulnerability when it was discovered, and devices were immediately at risk. In the meantime, the manufacturer has been able to provide an emergency update. Since attackers are constantly scanning the internet for security vulnerabilities with the help of search bots, it is easy for them to identify and attack a vulnerable device. In most cases, both the scanning and the attacks themselves are carried out by bots and are fully automated.
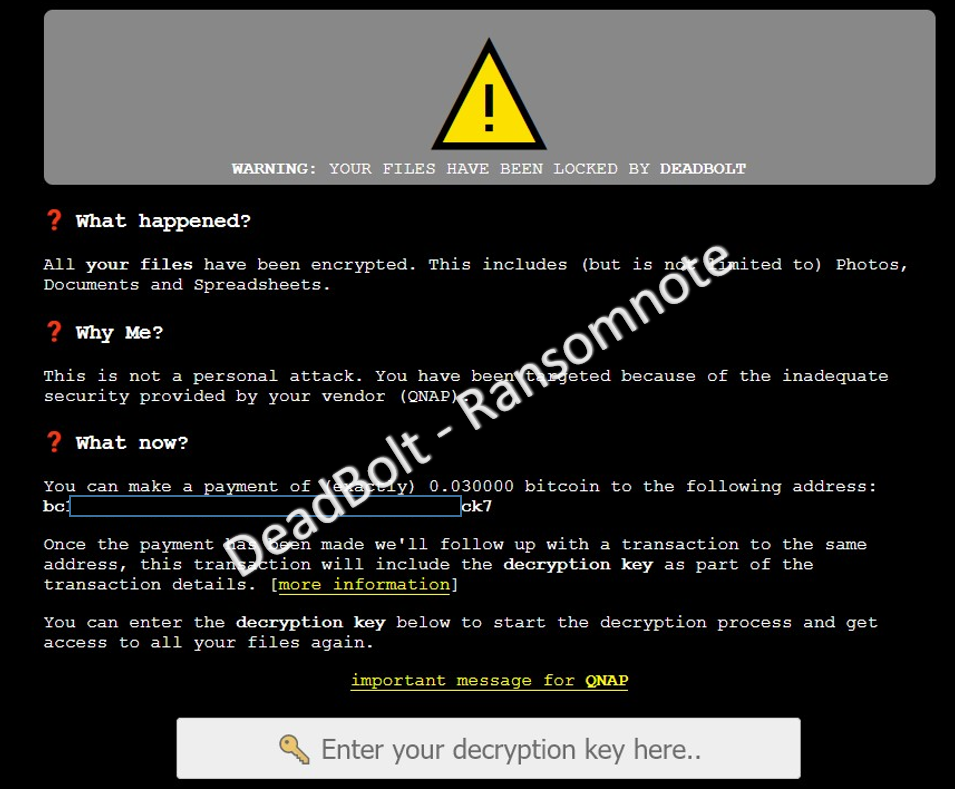
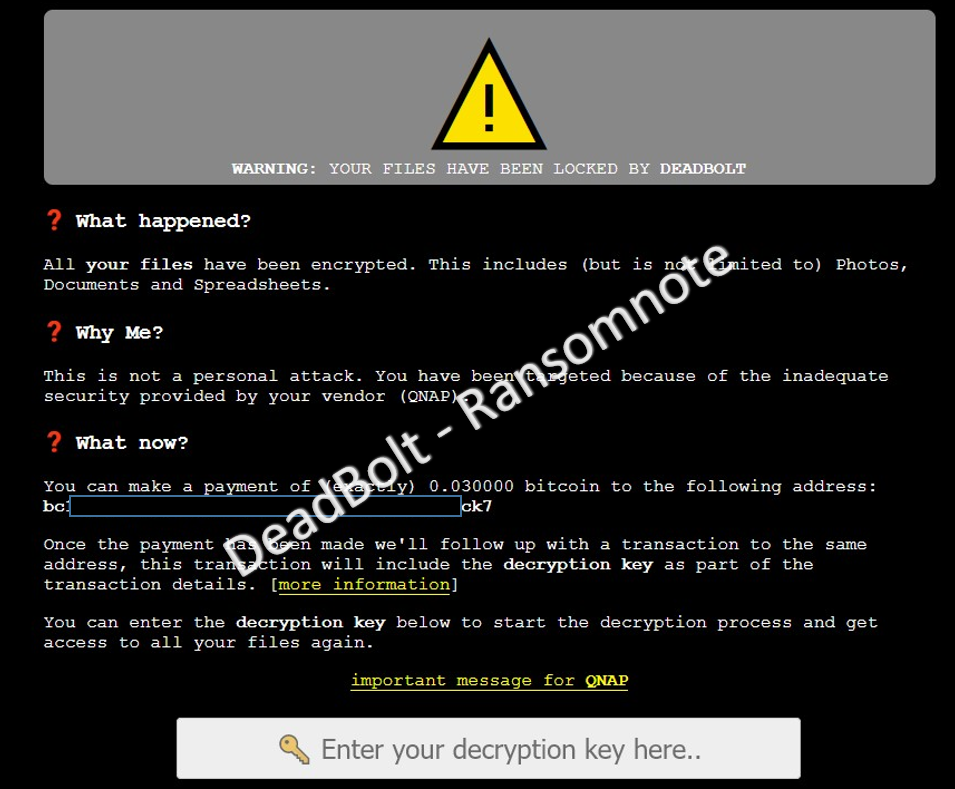
Whereas in the fourth quarter of 2021 it was mainly Qlocker malware that encrypted QNAP devices, now it is often DeadBolt ransomware.
On its homepage, the manufacturer informs its customers about the new security vulnerability and how devices can be secured.
The usual measures recommended to protect against this security vulnerability not only help against this current vulnerability, but also apply to all devices that are publicly accessible from the internet. Such devices are always exposed and can be attacked at any time. Therefore, if you do not want to be surprised by such attacks in the future, you should take the following precautionary measures:
- Install all currently available software updates as soon as they are released.
- Do not make your devices accessible from the internet. Where this is unavoidable, take additional measures, e.g. by using a virtual private network (VPN).
- Reduce the scope for attack from the internet and close all non-essential network ports. In particular, access points used for the administration of devices should not be accessible in an unprotected manner from the internet.
- Deactivate automatic network port forwarding on the router and on the NAS, in particular the UPnP service, which enables unchecked control of devices.
- Check your settings regularly by performing an appropriate network scan on the internet protocol (IP) address assigned to you (Online Port Scanner, NMAP).
- Immediately reset all passwords set by the manufacturer and define a new password. Always choose a strong, long password, and use two-factor authentication wherever possible.
Phishing email with an interesting attachment
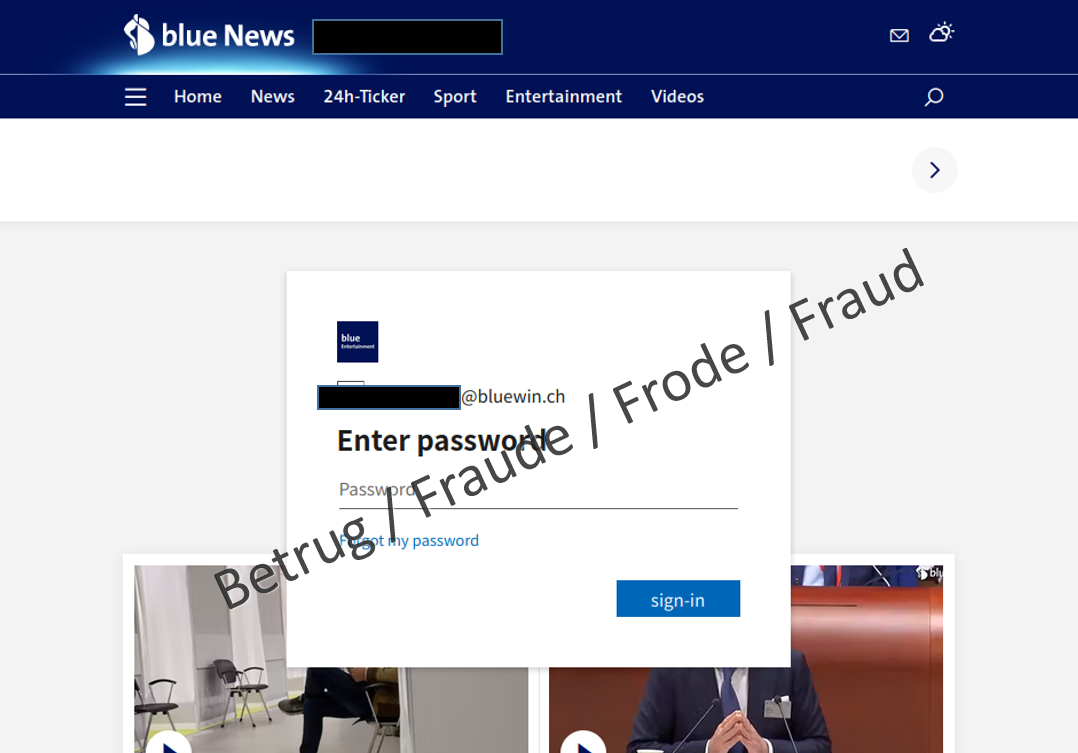
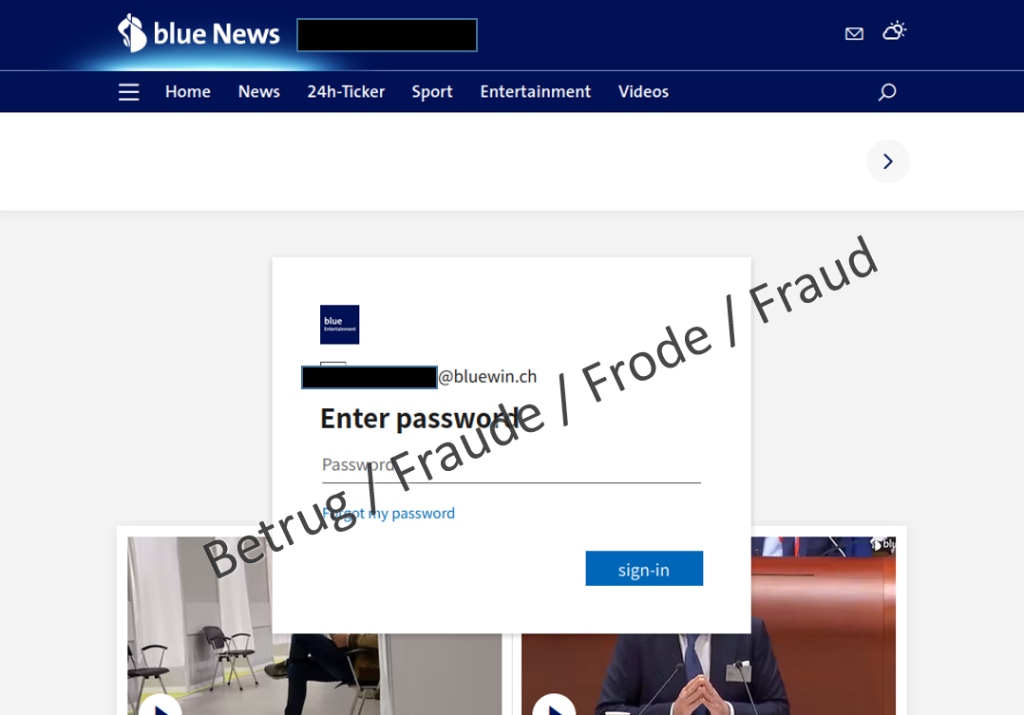
Last week, the NCSC had already received a message from a company which, at first glance, looked like a very targeted phishing attempt. A pop-up login window was displayed in the foreground and the company's website appeared greyed out in the background. We reported on this in the last weekly review. As usual, the phishing page in this case was stored on a website.
The NCSC has now been able to analyse a new attack technique in a reported phishing email.
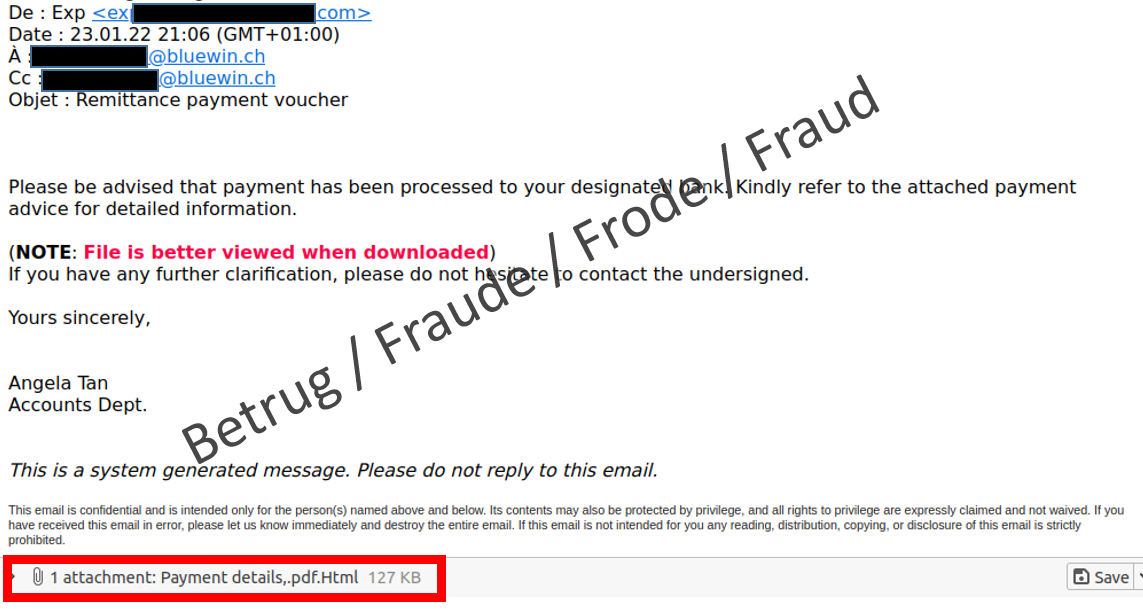
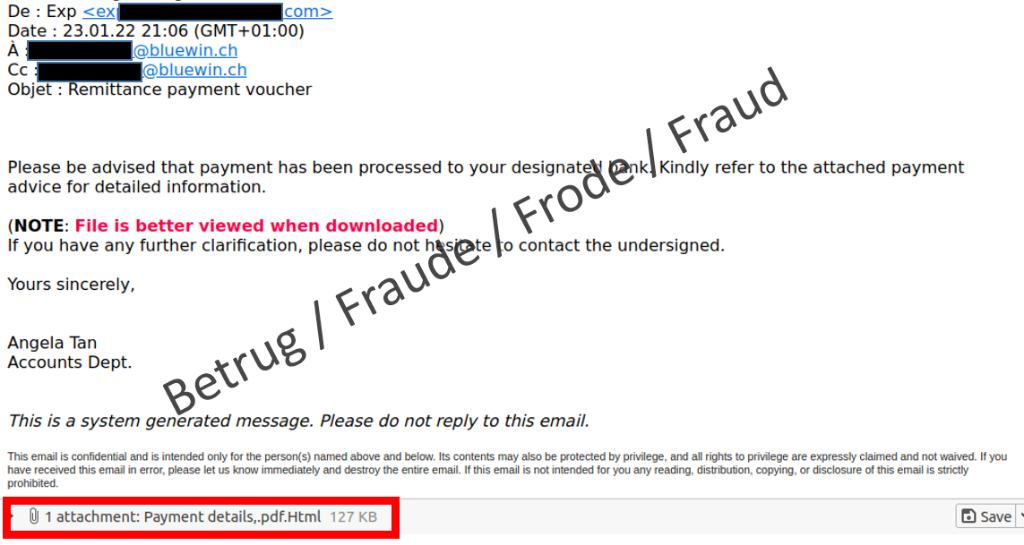
In contrast to usual mass phishing campaigns, the phishing email contained an attached document rather than a link. The attachment claimed to be a PDF, but in fact was an HTML file with JavaScript code and more than 400 lines of program code.
The NCSC opened the attached file in a secure environment. A browser was launched and the website of the email recipient's email provider appeared in the background, as in last week's case. An inconspicuous login window was displayed in the foreground. To someone who does not take any security measures and opens this attachment, it seems as if they have actually reached their provider's website.
By modifying the provider address, the NCSC was able to display the websites of other providers in the background. Here, too, the phishing email attachment loads the background that matches the email provider.
Website operators can prevent this from happening with relative ease. In the HTML header, meta tags can be used to specify whether a browser is allowed to display (embed) its own web pages in a third-party website or not. The browser will display either a warning message or an empty page.
- Never open attachments in emails that you were not expecting.
- Never enter a password on a page that you opened via a link.
- Check with the sender to make sure the email is really from them.
- Go directly to the sender's website and log in via the official website. In most cases, you can already check there whether the contents of the email are genuine.
- In general, always be suspicious of emails.
Current statistics
Last week's reports by category:
Last modification 01.02.2022