20.06.2023 - The QakBot malware is still active. With Microsoft severely restricting macro functions for documents obtained from the internet last year, the attackers are now trying other methods to trick their victims into clicking on an infected file and installing the malware.

The NCSC has already reported on the QakBot malware several times. The attackers tried to spread the malware via malicious macros in Word documents for a long time, even though documents from an unsecure source were opened in the protected view for quite a while and the macro function was thus disabled. In response to these precautionary measures, however, the fraudsters included instructions for the victims in the malicious documents, telling them how to enable macros nonetheless and thus deactivate the protection. The NCSC reported on this in weekly review 20
Microsoft responded last year after several attempts; macros in documents originating from the internet are now blocked and a red warning message is displayed. Unlike before, users can no longer bypass this block so easily. As a result, the NCSC also experienced a decrease in the number of reports concerning malicious macros.
However, the QakBot attackers are not giving up and are regularly testing new methods to install their malware on victims' computers. At the start of the year, primarily HTML smuggling variants were observed. In such cases, the malicious file is packed into the HTML code. When the HTML file attached to the email is opened, the page generates the malware on the fly and loads it directly onto the computer.
Two other methods were reported to the NCSC over the last few weeks, thereby showing that the attackers are experimenting and testing which method works best.
The trick with a non-existent page
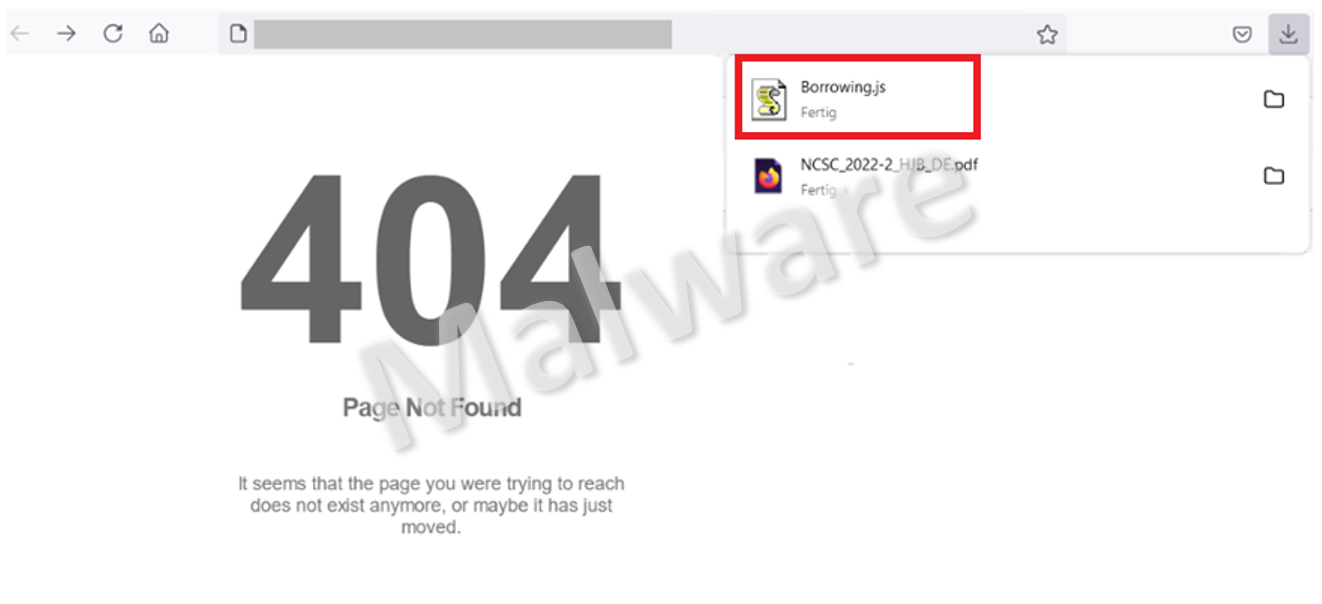
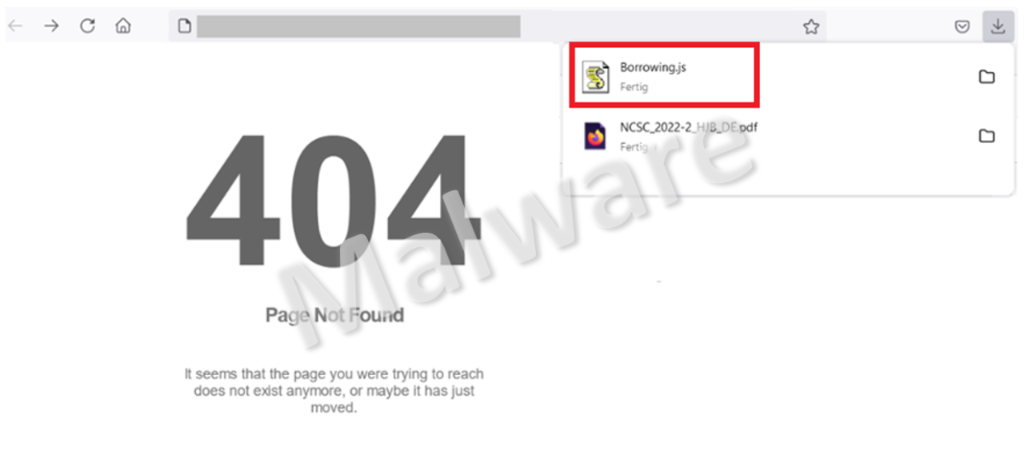
The newly reported variant also starts with an email and a link to be clicked on. Instead of a website being opened, though, an error message is displayed stating that the page was not found. In reality, the page was found but the fraudsters have prepared it in such a way that an error page is displayed in the foreground, while a JavaScript file is downloaded in the background. This file has an ever-changing and seemingly innocuous name that nonetheless arouses curiosity (e.g. Borrowing.js – the fraudsters hope that the victim will look in the Downloads folder to see what was borrowed). The file size also varies each time it is downloaded.
Displaying the error page is intended to conceal the file download in the background. Ideally, the victims should not be able to establish a link between the (apparently) faulty website and the file that suddenly appears. The attackers speculate that their victims will not notice the danger and will then open the file at some later date out of curiosity and thus execute it when they download other files, for instance, or check the Downloads folder.
To make matters worse, Windows does not display file extensions by default (in this case .js). Once the JavaScript file is executed, a PowerShell script is run in the background and goes unnoticed. This script then attempts to load the actual malicious code from the internet via a total of four IP addresses.
URL in a PDF – or the various steps leading to infection
In the second variant, an email is sent with an attached PDF file. Victims who open the PDF file are informed that the document contains protected files. They are prompted to click on "Open" to view them. After clicking, an empty page is opened in the browser. At the same time, a ZIP file is downloaded. The ZIP file contains the JavaScript file described above, which tries to connect to four IP addresses and download malicious code.
Publicly available threat lists include such malicious IP addresses. These lists are readily available, regularly updated and can be downloaded free of charge (e.g. at abuse.ch).
- Do not open files from unknown sources, and be especially wary of unknown files found in the Downloads folder.
- Malicious emails can also come from apparently known senders. Be careful if previous messages are suddenly used out of context, for example.
- Block access to known QakBot botnet C&C servers on your security perimeter (e.g. firewall, web proxy, etc.) using the Feodo Tracker Blocklist.
- Block access on your security perimeter (e.g. firewall, web proxy, etc.) to websites that are currently being used to spread malware. URLhaus offers corresponding lists in various formats.
Current statistics
Last week's reports by category:
Last modification 20.06.2023