31.08.2021 - The number of reports received by the NCSC increased again last week. There are still many reports concerning fake PostFinance pages opened via Google ads. The procedure is reminiscent of fake support calls. In addition, the victims of CEO fraud are being contacted not only via email, but also by phone. And it has become apparent that it is sometimes difficult for employees to recognise phishing emails with Office 365.

Fake Microsoft support staff are switching to e-banking fraud
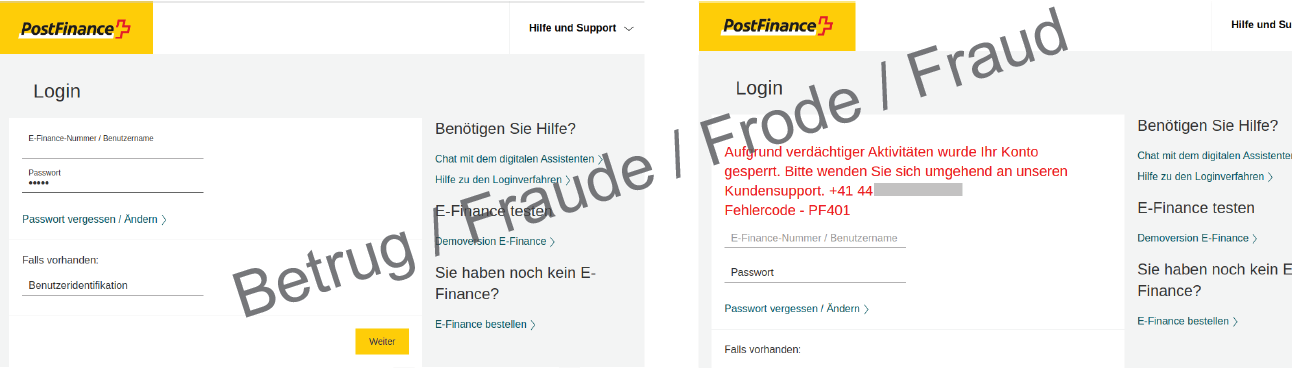
Already a fortnight ago (Week 32 in review), the NCSC reported on fake PostFinance websites: a Google search for the keywords "PostFinance" and "login" displays a Google ad that, at first glance, looks as if it is from "PostFinance". In this case, the fraudsters take advantage of the fact that many people do not enter the URL directly in the address bar or do not have the address in their bookmarks, and instead open the bank's login page via a Google search each time.
The link in this advertisement opens the homepage of a fake PostFinance e-banking portal. However, if you enter your login details and password, an error message appears telling you to call a Swiss telephone number.
Calls to this number are answered by an alleged support company based in Vienna masquerading as a partner of PostFinance. The support staff claim to have to verify the account and ask for a copy of the front and back of the person's ID card, among other things. Afterwards, the victim is supposed to install remote access software to enable the employee to access the computer and fix the "problem". Once the employee is connected to the victim's computer, a test transaction of CHF 2,000 is to be initiated. The victim is supposed to log into the e-banking account with the login details and password, as well as the second authentication factor. The support employee, who has full access to the computer thanks to the remote access software, now has the power to remotely initiate a "test payment" to any account.
The attackers spend a lot of time on these attempted attacks. The procedure takes up to 20 minutes. It is striking that the supposed support employees speak with an Indian accent in some cases. This is reminiscent of the fake Microsoft support calls during which a remote access tool is also supposed to be installed. Here, too, the attackers speak with an Indian accent. It seems that the fake support scammers are on the lookout for new areas of fraud.
- Always enter your bank's address by hand in the address bar, or use bookmarks.
- No bank or credit card company will ever send you an email requesting that you change your password or verify your credit card details.
CEO fraud now by phone too
CEO fraud is frequently reported to the NCSC. In this case, the attackers systematically search public company websites for the names and email addresses of CEOs and those in charge of the finance division. If the attackers find what they are looking for, a fake email ostensibly from the CEO is sent to the finance division and an urgent payment instruction is issued. The attackers usually avoid telephone contact and explicitly write in the emails that telephone queries are not possible. A telephone call would quickly blow the scam wide open, as the fraudsters do not speak the national languages without an accent and the victim would quickly realise that the person ordering the payment is not the CEO.
Interestingly, it was precisely this telephone approach that was chosen in a case reported to the NCSC last week. A person pretended to be the CEO and asked the employee in the finance division to make an urgent payment. Nevertheless, this new variant is only likely to work in large and international companies where the business language is English and employees are not familiar with the CEO's voice.
- Raise all employees' awareness of CEO fraud! Especially employees in finance divisions and in key positions must be informed about these possible methods of attack.
- In the case of associations, all presiding members and treasurers must receive training.
Office 365 phishing – install two-factor authentication wherever possible
So-called business email compromise is regularly reported to the NCSC. This type of fraud refers to an existing email that contains a payment instruction or invoice. The IBAN number to which the amount is to be paid is then altered. In order to access the email, attackers must have access to either the sender's or the recipient's email account.
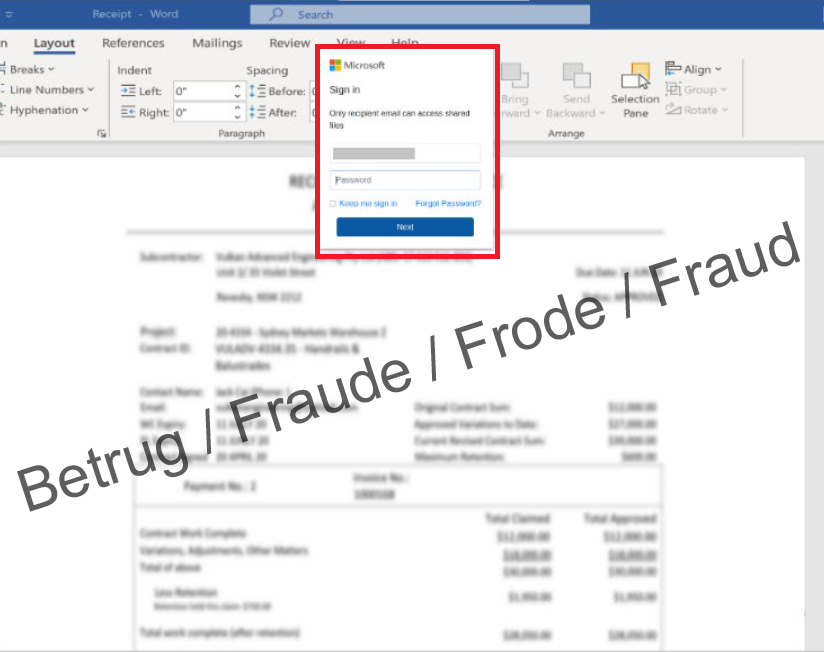
To obtain this access information, company employees usually receive a phishing email beforehand. A variant that is difficult to detect was reported to the NCSC last week. An employee received an email with an alleged project proposal to be downloaded from a server. Clicking on the link in the email opened a page which, blurred in the background, actually showed a supposed document.
However, the Office 365 password first had to be entered in order to open this document. Once these access credentials had been entered, the attackers had full access to the employee's email account.
- Wherever possible, install two-factor authentication. This offers an additional layer of protection to prevent your account from being hacked.
- Never divulge personal data such as passwords or credit card details on a website that you have accessed by clicking on a link in an email or text message.
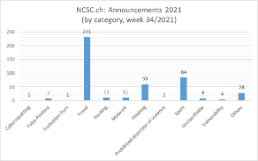
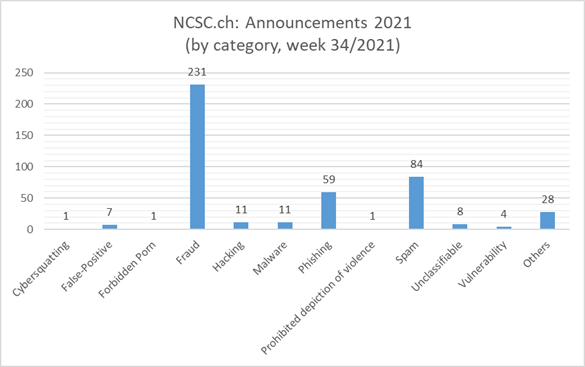
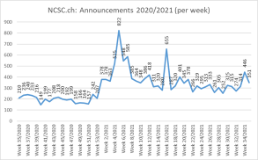
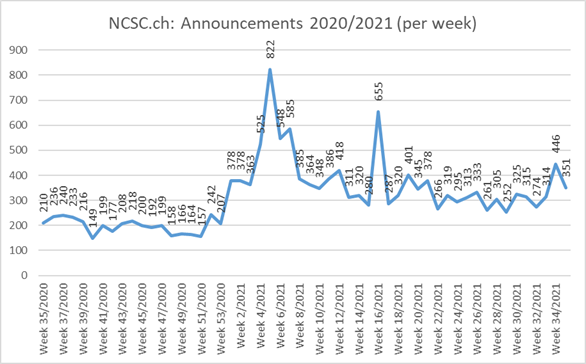
Current statistics
Last modification 31.08.2021