14.03.2022 - At the moment, cybercriminals are once again making increasing use of stolen email conversations to spread malware. This primarily affects companies, where employees who are contacted directly are used as a gateway for ransomware attacks. The origin of the current QakBot spam wave cannot be traced back to current events in connection with the Ukraine crisis.

For a few days now, the NCSC has been observing much activity involving QakBot (also known as QuakBot and QBot) in Switzerland. This is a type of malware that is spread via emails. The cybercriminals often use existing email conversations (e.g. with suppliers or clients) that have fallen into their hands through previous attacks, exploit them as a gateway to penetrate corporate networks unnoticed and then install encryption Trojans, i.e. ransomware. A QakBot infection often results in the encryption of company data and the attackers demanding that the companies pay a ransom. However, the NCSC strongly advises against paying a ransom and instead urges those affected to report the matter immediately to the prosecution authorities.
How malware is infiltrated into a corporate network
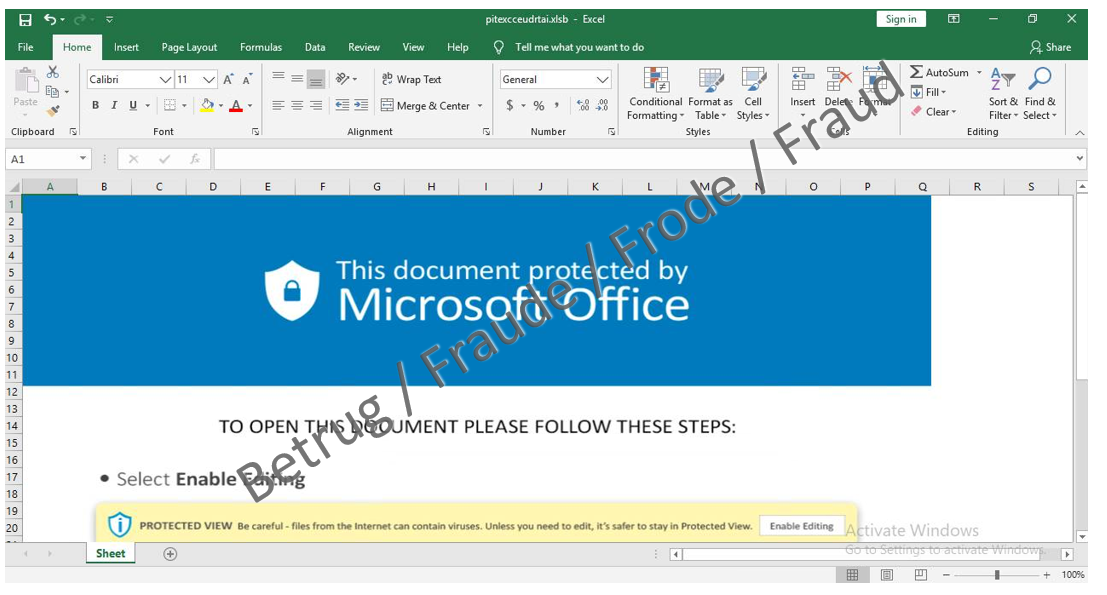
The origin of the current QakBot spam wave cannot be traced back to current events in connection with the Ukraine crisis, as the cybercriminals abuse existing, legitimate email conversations on other topics as a pretext to encourage the victim to click on a link (social engineering). The links in the emails appear unsuspicious, as they actually point to Microsoft's OneDrive cloud platform. However, once victims click on the link, they are taken to a password-protected ZIP archive on OneDrive. This contains an Excel file which infects the victims' computers with QakBot when the macros it contains are executed.
The modus operandi described is not new. Back in December 2021, the NCSC warned of similar attacks using the malware Emotet. It seems, however, that the attackers are spreading the malware exclusively via Microsoft OneDrive rather than as an email attachment in the current spam wave. This allows many spam and virus filters to be tricked, leading to a heightened risk of exposure for companies.
Tips to protect yourself from malware
- Be careful when opening email attachments, even if they come from a supposedly trustworthy source.
- Be careful when using Microsoft OneDrive, especially when dealing with password-protected ZIP archives. Do not follow any links to OneDrive, even if they come from a supposedly trustworthy source.
- Never activate macros ("Enable Content") when opening a document (Word, Excel)
The NCSC also recommends the following measures for companies:
- Block the receipt of dangerous email attachments on your email gateway. This includes Office documents with macros. A recommended list of file types to block can be found here:
https://www.govcert.ch/downloads/blocked-filetypes.txt. - If your company does not use Microsoft OneDrive for business purposes, we recommend that you block access to Microsoft OneDrive (onedrive.live.com), at least temporarily, on the security perimeter (e.g. firewall, web proxy, etc.).
- Block access to known QakBot botnet C&C servers on your security perimeter (e.g. firewall, web proxy, etc.) using the Feodo Tracker Blocklist.
- Block access on your security perimeter rity perimeter (e.g. firewall, web proxy, etc.) to websites that are currently being used to spread malware. URLhaus offers the corresponding list in various formats.
Report suspicious emails
Report suspicious emails (phishing or malware) to the NCSC at: antiphishing.ch.
If you are not sure about an email, or if you would like feedback, use the NCSC reporting form.
Among other things, your report will help to ensure a better picture of the cybersituation and allow the NCSC to take appropriate
defensive measures if necessary.
Previous news items:
Last modification 14.03.2022